- Manuals
- Brands
- Konica Minolta Manuals
- All in One Printer
- bizhub C368
Manuals and User Guides for Konica Minolta bizhub C368. We have 9 Konica Minolta bizhub C368 manuals available for free PDF download: Service Manual, Quick Start Manual, Quick Manual, Product Manual, Installation Manual, Quick User Manual, Installation Instructions

- Manuals
- Brands
- Konica Minolta Manuals
- All in One Printer
- bizhub C368
- Quick manual
-
Contents
-
Table of Contents
-
Troubleshooting
-
Bookmarks
Quick Links
bizhub C368/C308
QUICK GUIDE
Related Manuals for Konica Minolta bizhub C368
Summary of Contents for Konica Minolta bizhub C368
-
Page 1
C368/C308 QUICK GUIDE… -
Page 3: Table Of Contents
Data stored in this machine ………………….1-18 Legal restrictions on reproduction………………..1-19 1.10 Trademark acknowledgements ………………..1-20 Copyright ……………………….1-21 Note …………………………1-21 1.11 SOFTWARE LICENSE AGREEMENT ………………. 1-22 1.12 i-Option LK-105 v4 (searchable PDFs) End User License Agreement ……..1-24 bizhub C368/C308 Contents-1…
-
Page 4
Precautions on using the Touch Panel ……………….. 2-29 2.6.4 How to display the Keypad…………………..2-30 How to move the Keypad …………………… 2-30 How to close the Keypad……………………. 2-30 To display the Keypad all the time………………..2-31 2.6.5 Entering characters………………………2-31 When typing in «Group1»: …………………… 2-31 Contents-2 bizhub C368/C308… -
Page 5
Operation flow……………………..3-14 Checking the cable connection ………………….. 3-14 Checking network settings of this machine ………………3-15 Checklist ……………………….3-15 Checking computer information …………………. 3-16 Configuring your computer ………………….3-16 Registering destinations ……………………3-17 Sending the original ……………………. 3-19 bizhub C368/C308 Contents-3… -
Page 6
Getting help on the currently displayed screen: …………….3-66 Getting help on the desired function or procedure:…………….. 3-68 Help Menu list ……………………..3-70 Using the [Quick Security] function ……………….. 3-71 3.8.1 [Quick Security] ……………………..3-71 Required settings ……………………..3-71 Contents-4 bizhub C368/C308… -
Page 7
When it is time to replace a Developing Unit………………. 5-12 When a Waste Toner Box is full ………………….. 5-13 5.5.1 Replacing a Toner Cartridge ………………….5-14 5.5.2 Replacing a Waste Toner Box ………………….5-15 5.5.3 Replacing a Drum Unit……………………5-17 Index Index by item ……………………… 6-3 bizhub C368/C308 Contents-5… -
Page 8
Contents-6 bizhub C368/C308… -
Page 9: Introduction
Introduction…
-
Page 11
The illustrations and screens used in this manual may appear slightly different from views of the actual equip- ment and screens. Tips Please keep this manual as well as the attached CD/DVD in a safe place where you can access them easily. bizhub C368/C308… -
Page 12: Environmental Information
With a product which has a duplex unit, you can print on both sides of paper automatically. Using this function leads to reducing consumption of natural resources and your cost. Attached printer driver provides this duplex printing function as initial setting in your computer (The setting can be changed after installation manually). bizhub C368/C308…
-
Page 13: Certification For Usa, Canada, Mexico, Brazil And Europe Area
Certification for USA, Canada, Mexico, Brazil and Europe area For U.S.A This product is certified by the following model name in U.S.A. KONICA MINOLTA branded model C302301 (bizhub C368, bizhub C308). For Canada This product is certified by the following model name in Canada.
-
Page 14: Safety Information
The power cord meets regulatory requirements for the area. • The power cord is provided with grounding pin/terminal. Do not use the power cord to other products. Failure to do that could re- sult in a fire or electrical shock. bizhub C368/C308…
-
Page 15
Remove the power plug from the outlet more than one time a year and clean the area between the plug terminals. Dust that accumulates be- tween the plug terminals may cause a fire. bizhub C368/C308… -
Page 16: Installation
When moving this product, always hold it at the locations specified in the User’s Guide or other documents. If the unit is moved while held at loca- tions other than those specified, it may fall, causing severe personal in- jury. bizhub C368/C308…
-
Page 17: Using The Product
«Caution HOT» caution label. A burn could result. Unplug the product when you will not use the product for long periods of time. When using the machine, do not look at the light of the lamp for a pro- longed time. Eyestrain could result. bizhub C368/C308…
-
Page 18: Consumables
Then, leave the machine to stand idle for a specified period of time and make sure that the fusing section has cooled down to room temperature. Failure to follow these in- structions could result in a burn. 1-10 bizhub C368/C308…
-
Page 19: Regulation Notices
CISPR rules and local rules. GS Certification KONICA MINOLTA branded model C302301 (bizhub C368, bizhub C308). Laser safety This is a digital machine which operates using a laser. There is no possibility of danger from the laser provided the machine is operated according to the instructions in the manuals.
-
Page 20: Internal Laser Radiation
Regulation notices Internal laser radiation Maximum Average Radiation Power: 8.1 μW (bizhub C368) / 7.1 μW (bizhub C308) at the laser aperture of the print head unit. Wavelength: 770-800 nm This product employs a Class 3B laser diode that emits an invisible laser beam.
-
Page 21: Laser Safety Label
Recycling of this product will help to conserve natural resourc- es and prevent potential negative consequences for the environment and human health caused by inappropriate waste handling. This product complies with RoHS (2011/65/EU) Directive. bizhub C368/C308 1-13…
-
Page 22: Telephone Cable (For Users In Countries Subject To Class B Regulations)
STAND-BY push-push type bonding terminal Protective earthing switches CLASS II EQUIP- Class II equipment Functional earthing MENT with functional earthing General precaution High temperature Electrical shock hazard CAUTION CAUTION moving fan blade DOUBLE POLE / NEUTRAL FUSING 1-14 bizhub C368/C308…
-
Page 23: Caution Notations And Labels
Do not remove caution labels or notations. If any caution label or caution notation is soiled, please clean to make legible. If you cannot make them legible, or if the caution label or notation is damaged, please contact your service representative. bizhub C368/C308 1-15…
-
Page 24: Special Notice To User
PSTNs provided in different countries, the approval does not, of itself, give an unconditional assurance of successful operation on every PSTN network terminal point. In the event of problems, you should contact your equipment supplier in the first instance. 1-16 bizhub C368/C308…
-
Page 25: Space Requirements
48-13/16 (1240) 25-7/8 38-13/16 18-7/8 16-7/8 31-15/16 (428) (812) (658) (986) (480) bizhub C368/C308 + DF-629 + PC-210 + FS-534 + SD-511 + RU-513 + LU-302 Unit: inch (mm) 43-6/9 (1107) 49-1/16 (1246) 6-11/16 36-7/8 16-7/8 32-3/16 (170) (937) (428)
-
Page 26: Operation Precautions
For details of the overwrite all data function, refer to the User’s Guide. Contact your service representative before deleting data. It is recommended to backup HDD periodically as the measures for HDD defect. For the detail information of HDD backup, contact your service representative. 1-18 bizhub C368/C308…
-
Page 27: Legal Restrictions On Reproduction
This machine provides the forgery prevention function in order to prevent financial instruments from being re- produced illegally. We appreciate your understanding that printed images may infrequently have some noise or image data may not be stored under certain circumstances due to this forgery prevention function. bizhub C368/C308 1-19…
-
Page 28: Trademark Acknowledgements
1.10 1.10 Trademark acknowledgements KONICA MINOLTA, the KONICA MINOLTA logo, Giving Shape to Ideas, PageScope, and bizhub are regis- tered trademarks or trademarks of KONICA MINOLTA, INC. Mozilla and Firefox are trademarks of the Mozilla Foundation. Novell and Novell NetWare are registered trademarks of Novell, Inc. in the United States and other countries.
-
Page 29: Copyright
Note User’s Guide may not be reproduced in part or in full without permission. KONICA MINOLTA, INC. will not be held liable for any incidents caused by using this printing system or Us- er’s Guide. Information included in User’s Guide is subject to change without notice.
-
Page 30: Software License Agreement
Software, (b) such transfer of possession terminates your license from Konica Minolta, and (c) you must assure that such other party has agreed to accept and be bound by the terms and conditions of this Agreement. If such other party does not accept such terms and con- ditions then you shall not transfer any copy of the Software.
-
Page 31
BOUND BY ITS TERMS AND CONDITIONS. NEITHER PARTY SHALL BE BOUND BY ANY OTHER STATE- MENTS OR REPRESENTATIONS THAT ARE INCONSISTENT WITH THE TERMS AND CONDITIONS OF THIS AGREEMENT. NO AMENDMENT TO THIS AGREEMENT IS EFFECTIVE UNLESS IN WRITING AND SIGNED BY DULY AUTHORIZED REPRESENTATIVES OF EACH PARTY. bizhub C368/C308 1-23… -
Page 32: I-Option Lk-105 V4 (Searchable Pdfs) End User License Agreement
This license shall automatically terminate upon a failure on your part to comply with any term or condi- tion of this Agreement, in which case you agree to immediately stop use of the Program. This Agreement shall be governed by the laws of Japan. 1-24 bizhub C368/C308…
-
Page 33: About This Machine
About This Machine…
-
Page 35: Intended Use Of Office Mfp Devices
Errors or damage have been discovered, Maintenance intervals have been exceeded, Mechanical or electrical functions do not work as they should. Exclusion of liability The manufacturer of the system assumes no liability for damages if the system was operated under imper- missible conditions. bizhub C368/C308…
-
Page 36: Introduction To User’s Guide
Select a desired function on the top page (Home), and check the details of the function. Selecting [Introduction] on the top page (Home) allows you to view detailed methods for using the User’s Guide. bizhub C368/C308…
-
Page 37: Layout Of Top Page
• Check that JavaScript in your Web browser is enabled. The Us- er’s Guide uses JavaScript for the page display and search func- tions. 1024 e 768 pixels or more Display resolution bizhub C368/C308…
-
Page 38: Target Groups
This symbol indicates a risk that may result in damage to this machine or documents. Follow the instructions to avoid property damage. Tips This symbol indicates supplemental information of a topic as well as options required to use a function. Reference This symbol indicates reference functions related to a topic. bizhub C368/C308…
-
Page 39: Notations Of Application Names
This manual describes application names as shown below. Application name Notations used in this manual PageScope Web Connection Web Connection PageScope My Panel Manager My Panel Manager PageScope Mobile (for iPhone/iPad/Android) Mobile (for iPhone/iPad/Android) bizhub Remote Access Remote Access bizhub C368/C308…
-
Page 40: About This Machine
About this machine About this machine 2.3.1 Optional components Various optional components can be added to meet your office requirements. List of optional components bizhub C368/C308…
-
Page 41
110, or Paper Feed Cabinet PC-210 must be installed on this ma- chine. Saddle Stitcher SD-511 Used to add the fold/center staple function to the Finisher FS-534. Punch Kit PK-520 Used to add the punch function to the Finisher FS-534. Relay Unit RU-513 Required to install the Finisher FS-534. bizhub C368/C308… -
Page 42: List Of Other Optional Components
Prevents paper in a paper tray from being affected by humidity. The Heater can be mounted when you purchase Paper Feed Cab- inet PC-110, Paper Feed Cabinet PC-210, or Paper Feed Cabi- net PC-410. Power Supply BOX Used to turn Heater operations on or off. MK-734 2-10 bizhub C368/C308…
-
Page 43
Mount Kit MK-735 Required to use the machine unit that has Authentication Unit AU-201S (IC Card Type) built in to it. Hard Disk HD-524 Install this unit to perform mirroring of the hard disk contained in the main unit. bizhub C368/C308 2-11… -
Page 44: Name Of Parts (Mfp)
Flashes blue while this machine is receiving a job. If a job is current- ly spooled, this indicator lamp lights up blue. Status Indicator Flashes white during printing. Warning Indicator Flashes orange if a warning occurs. Lights up orange if this machine has stopped due to an error. 2-12 bizhub C368/C308…
-
Page 45: Right Side/Rear Side
Jack for connecting a telephone (TEL PORT1) Telephone Jack 1 (LINE PORT1) Telephone Jack 2 (LINE PORT2) USB Port (Type A) USB2.0/1.1 Network Connector (10Base-T/100Base-TX/1000Base-T) USB Port (Type B) USB2.0/1.1 Reference For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-13…
-
Page 46: Name Of Parts (Optional Units)
Name of parts (Optional units) This section shows the names of distinctive parts for each optional unit that can be installed in this machine. Finisher FS-533, Punch Kit PK-519 Name Punch Kit Staple Cartridge Output Tray Tray Extension 2-14 bizhub C368/C308…
-
Page 47: Job Separator Js-506
About this machine Job Separator JS-506 Name Output Tray bizhub C368/C308 2-15…
-
Page 48: Finisher Fs-534, Saddle Stitcher Sd-511, Punch Kit Pk-520
About this machine Finisher FS-534, Saddle Stitcher SD-511, Punch Kit PK-520 Name Output Tray Staple Cartridge Punch Scrap Box Saddle Stitcher 2-16 bizhub C368/C308…
-
Page 49
About this machine Name Punch Kit Staple Cartridge Folding Output Tray bizhub C368/C308 2-17… -
Page 50: Large Capacity Unit Lu-302
About this machine Large Capacity Unit LU-302 2-18 bizhub C368/C308…
-
Page 51: Power Supply
Open the Front Door, and press n on the Main Power Switch. Press o on the Main Power Switch. NOTICE To restart this machine, turn the Main Power Switch off and on again after 10 or more seconds have passed. bizhub C368/C308 2-19…
-
Page 52: Operating The Power Key
This machine can receive data or faxes, but cannot scan or print an original. If data or faxes are received when the machine is in the Sub Power OFF mode, they are printed when the machine returns to the normal mode. Normal mode During opera- Lights up blue. tion 2-20 bizhub C368/C308…
-
Page 53: Power Save Function
To enable the machine to return to the normal mode from the Sub Power OFF or ErP Auto Power OFF mode, press the Power key again. Reference For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-21…
-
Page 54: Control Panel
Press this key to reset all settings, excluding the registered ones, that you entered using the Control Panel. Stop Press this key to temporarily stop an active copy, scan, or print job. Start Press to start the copy, scan or fax operation. 2-22 bizhub C368/C308…
-
Page 55
Use this Keypad to enter numeric values such as the number of copies, zoom ratio, and fax number. C (Clear) Press this key to cancel numeric values such as the number of cop- ies, zoom ratio, and size you entered using the Keypad. bizhub C368/C308 2-23… -
Page 56: Touch Panel
Tap this button to configure settings of this machine or view the use status of this machine. • [Utility] is always displayed. Page switching key Tap this key to switch pages when main menu keys are assigned to multiple pages. 2-24 bizhub C368/C308…
-
Page 57: Customizing The Main Menu
In addition, you can specify your favorite background pattern. If necessary, you can add a background pat- tern by registering an image on this machine. Reference For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-25…
-
Page 58: Slide Menu
Up to five slide menus can be set. You can configure the setting to prevent the slide menu. Also, you can display the Keypad or change the background color. Reference For details, refer to the User’s Guide CD/DVD. 2-26 bizhub C368/C308…
-
Page 59: Operating The Touch Panel
User Box. Flick Make a slight fillip while sliding your finger on the screen. Used to scroll the destination/job list or to feed a page in the Main menu screen/Preview screen. bizhub C368/C308 2-27…
-
Page 60: Drag
Hold down the document by the finger. Used to display the icon re- lated to the document. Drag & Drop Slide your finger to the intended place and release it while a doc- ument is selected. Used to move the document to the intended place. 2-28 bizhub C368/C308…
-
Page 61: Pinch In/Pinch Out
20 inches (50 cm) or less while you are operating the Touch Panel. Avoid using the Touch Panel at a site near a device that generates electric noise (such as a generator and an air conditioner). The electric noise may cause the Touch Panel to operate erratically. bizhub C368/C308 2-29…
-
Page 62: How To Display The Keypad
Move your finger while the upper side of Keypad is being pressed. How to close the Keypad After entering, tap [Close] to close the Keypad. It can also be closed by pressing the 10 Keypad key (default: Reg- ister key 3). 2-30 bizhub C368/C308…
-
Page 63: To Display The Keypad All The Time
] or [ ] to move the cursor to the character you want to clear, then tap the [Delete] key. % Tap the [Shift] key again to return to the original keyboard screen. After typing completes, tap [OK]. bizhub C368/C308 2-31…
-
Page 64: Jobs
The table below shows the maximum number of jobs that can be registered for each function. Function Minimum number of jobs Maximum number of jobs Copy Print Fax memory TX + Scan Fax RX Sharing These values may vary depending on conditions. 2-32 bizhub C368/C308…
-
Page 65: Loading Paper
Load paper into the tray. % Load paper into the tray with the print side facing up. When loading paper other than plain paper, specify the paper type. % For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-33…
-
Page 66: Lct (Built-In)
Load paper into the left tray. % Load paper into the tray with the print side facing up. When loading paper other than plain paper, specify the paper type. % For details, refer to the User’s Guide CD/DVD. 2-34 bizhub C368/C308…
-
Page 67: Loading Paper Into The Large Capacity Unit
Do not load the Large Capacity Unit with paper of a size other than that previously specified. To change the paper size, con- tact your service representative. When loading paper other than plain paper, specify the paper type. % For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-35…
-
Page 68: Bypass Tray
Paper not available Do not load the following paper into the Bypass Tray. Doing so may cause a paper jam or damage to the machine. Folded, torn or creased paper, or bundles of sheets of different sizes 2-36 bizhub C368/C308…
-
Page 69: How To Load Paper
Select the paper type and paper size. % When loading paper other than plain paper, change the paper type setting. % When loading custom sized paper, change the paper type setting. % For details, refer to the User’s Guide CD/DVD. bizhub C368/C308 2-37…
-
Page 70: Loading Postcards
When loading postcards into the Bypass Tray, note the following points. When loading curled postcards, uncurl the postcards as shown in the figure in advance. Do not put spare postcards in the Bypass Tray. Doing so causes a size detection error. 2-38 bizhub C368/C308…
-
Page 71: Loading Transparencies
% Select [Paper] — [#] — [Change Tray Setting] — [Paper Type] — [Transparency]. % Transparencies can only be printed in black. When the color function is other than black and [Trans- parency] is selected, check the displayed message, and tap [Yes]. bizhub C368/C308 2-39…
-
Page 72: Loading Envelopes
Do not use envelopes that have glue or release paper on the flaps or the part covered by the flap on the body. Otherwise, the machine may be damaged or a failure may occur. 2-40 bizhub C368/C308…
-
Page 73
When loading envelopes with flaps opened, also select the standard size that matches them. You do not have to measure the size of the envelope with the flap opened to set the size as a custom-sized enve- lope. bizhub C368/C308 2-41… -
Page 74: Loading Label Sheets
Lateral Guide to the paper. % Insert label sheets into the tray until their edges are pressed against the back. Change the paper type setting. % Select [Paper] — [#] — [Change Tray Setting] — [Paper Type] — [Thick 1+]. 2-42 bizhub C368/C308…
-
Page 75: Loading Index Papers
Lateral Guide to the paper. % Insert index papers into the tray until their edges are pressed against the back. Change the paper type setting. % Select [Paper] — [#] — [Change Tray Setting] — [Paper Type] — [Index Paper]. bizhub C368/C308 2-43…
-
Page 76
Loading paper 2-44 bizhub C368/C308… -
Page 77: Basic Settings And Operations
Basic Settings and Operations…
-
Page 79: Print Function
The following describes a flow to print data from your computer. For details, refer to page 3-5. Opening original data % Open the data you want to print using the application software. Configuring the printer driver for printing % Select a printer driver, and change the setting if necessary before printing. bizhub C368/C308…
-
Page 80: Checking The Cable Connection
If no IP address is displayed, you need to configure the network. Tap [Utility], and select [Administrator Settings] — [Network Settings] — [TCP/IP Settings]. Configure the required settings to suit your environ- ment. For details, refer to the User’s Guide CD/DVD. For information on the default administrator password, refer to the User’s Guide CD/DVD. bizhub C368/C308…
-
Page 81: Installing The Printer Driver
Select the installed printer driver, and click [Print]. Tips Clicking [Preferences] can change the setting of the printer driver as required. If user authentication is enabled in this machine, specify the required data such as the user name and password. bizhub C368/C308…
-
Page 82: Types Of Printer Drivers
% Install the printer driver on the computer. For details, refer to page 3-10. Adding and configuring a printer driver % Set up your computer so that data can be printed using the installed printer driver. For details, refer to page 3-11. bizhub C368/C308…
-
Page 83: Operation Flow
% Select a printer driver, and change the setting if necessary before printing. Checking the cable connection Check that a LAN cable is connected to the LAN port of this ma- chine and the green LED is on. bizhub C368/C308…
-
Page 84: Checking Network Settings Of This Machine
Specify the Bonjour name. Tap [Utility], and select [Administrator Settings] — [Network Settings] — [Bon- jour Setting] — [ON]. % For information on the default administrator password, refer to the User’s Guide CD/DVD. % The Bonjour name is displayed on the printer driver as a connected device name. bizhub C368/C308…
-
Page 85
If no IP address is displayed in Step 1, you need to set up the network. Tap [Utility], and select [Admin- istrator Settings] — [Network Settings] — [TCP/IP Settings]. Configure the required settings to suit your environment. For details, refer to the User’s Guide CD/DVD. For information on the default administrator password, refer to the User’s Guide CD/DVD. bizhub C368/C308… -
Page 86: Installing The Printer Driver
Proceed with the procedure according to the on-screen instructions until the installation screen ap- pears. Click [Install]. When a prompt message appears to ask you to enter the name and password, type in the name and password of the user with administrator privileges. Click [Close]. 3-10 bizhub C368/C308…
-
Page 87: Adding And Configuring A Printer Driver
Printing data Open the data you want to print using the application software. From the [File] menu, select [Print]. Select the Bonjour name of this machine. Tips If necessary, you can change the settings of the printer driver. bizhub C368/C308 3-11…
-
Page 88: Scan-To-Send Function
Send scanned data as an E-mail attachment. This function is useful when you want to forward data to an outside location. For details, refer to page 3-29. Saving data to the USB memory device (External memory) Directly save scanned data on the USB memory device connected to this machine. For details, refer to page 3-61. 3-12 bizhub C368/C308…
-
Page 89: Various Methods For Transmitting And Saving Data
Sending to a WebDAV server (WebDAV Send) Reference For details, refer to the User’s Guide CD/DVD. 3.2.2 Sending data to your Windows computer (SMB Send) Send scanned data to a computer on the network. Once settings are configured, you can send data easily. bizhub C368/C308 3-13…
-
Page 90: Preparation Flow
Press the Start key. % Press the Start key to scan the original. Checking the cable connection Check that a LAN cable is connected to the LAN port of this ma- chine and the green LED is on. 3-14 bizhub C368/C308…
-
Page 91: Checking Network Settings Of This Machine
User ID User name required to log in to the computer page 3-16 Password Password required to log in to the computer Contact your sys- • You should not enter this column for security reasons. tem administra- tor. bizhub C368/C308 3-15…
-
Page 92: Checking Computer Information
Configure the setting to share the folder created in Step 2. Right-click on the folder, then click [Proper- ties]. Click the [Sharing] tab, then click [Advanced Sharing]. Select the [Share this folder] check box, then click [Permissions]. Select [Everyone] from the [Group or user names:] list, then select all of the [Allow] check boxes. 3-16 bizhub C368/C308…
-
Page 93: Registering Destinations
For [Name], specify the name to be displayed on the assigned key. % For [Sort Character], enter the same name as [Name]. % This sets the appropriate index for the name, which you entered into [Name], to [Index]. To change the setting, tap [Index]. bizhub C368/C308 3-17…
-
Page 94
While checking the checklist, enter the host address and file path you wrote down. % When not specifying a folder, enter a slash «/» for the file path. When specifying a folder, enter only the folder name without slash «/». Tap [Close]. 3-18 bizhub C368/C308… -
Page 95: Sending The Original
Scan-to-Send function Sending the original Load the original. Tap [Scan/Fax]. Select a destination. bizhub C368/C308 3-19…
-
Page 96
Select the type of the file to save scanned data. [Scan Size] Specify the size of the original to be scanned. [File Name/Subject Change the file name or the subject of an E-mail to be sent. Name/Other] Press the Start key. 3-20 bizhub C368/C308… -
Page 97: Sending Data To Your Mac Computer (Smb Send)
The following describes a transmission flow. For details, refer to page 3-27. Loading the original Selecting a destination % Select a registered destination, and check the settings such as the file type and image quality. Press the Start key. % Press the Start key to scan the original. bizhub C368/C308 3-21…
-
Page 98: Checking The Cable Connection
Settings] — [Network Settings] — [TCP/IP Settings]. Configure the required settings to suit your environ- ment. For details, refer to the User’s Guide CD/DVD. For information on the default administrator password, refer to the User’s Guide CD/DVD. 3-22 bizhub C368/C308…
-
Page 99: Configuring This Machine (Mac Os X 10.7 Or Later)
Select [ON] in [Utility] — [Administrator Settings] — [Network Settings] — [SMB Settings] — [Direct Hosting Setting], then tap [OK]. Select [Utility] — [Administrator Settings] — [System Settings] — [Date/Time Settings] to specify the same date/time and time zone between this machine and your computer, then tap [OK]. bizhub C368/C308 3-23…
-
Page 100: Checklist
Select the [Share files and folders using SMB (Windows)] and user name check boxes, then click [Done]. Under [Shared Folders:], click [+]. Select a new folder. Click the new folder to check the access right. If the access right is changed to [Read & Write], the setting is completed. 3-24 bizhub C368/C308…
-
Page 101: Registering Destinations
For [Name], specify the name to be displayed on the assigned key. % For [Sort Character], enter the same name as [Name]. % This sets the appropriate index for the name, which you entered into [Name], to [Index]. To change the setting, tap [Index]. bizhub C368/C308 3-25…
-
Page 102
While checking the checklist, enter the host address and file path you wrote down. % When not specifying a folder, enter a slash «/» for the file path. When specifying a folder, enter only the folder name without slash «/». Tap [Close]. 3-26 bizhub C368/C308… -
Page 103: Sending The Original
Scan-to-Send function Sending the original Load the original. Tap [Scan/Fax]. Select a destination. bizhub C368/C308 3-27…
-
Page 104
Select the type of the file to save scanned data. [Scan Size] Specify the size of the original to be scanned. [File Name/Subject Change the file name or the subject of an E-mail to be sent. Name/Other] Press the Start key. 3-28 bizhub C368/C308… -
Page 105: Transmit The Scanned Data Via E-Mail (E-Mail Tx)
Loading the original Entering a destination % Enter the destination E-mail address, and check the settings such as the file type and image quality. Press the Start key. % Press the Start key to scan the original. bizhub C368/C308 3-29…
-
Page 106: Checking The Cable Connection
Settings] — [Network Settings] — [TCP/IP Settings]. Configure the required settings to suit your environ- ment. For details, refer to the User’s Guide CD/DVD. For information on the default administrator password, refer to the User’s Guide CD/DVD. 3-30 bizhub C368/C308…
-
Page 107: Configuring The E-Mail Transmission Environment
Tap [Utility], and select [Administrator Settings] — [Network Settings] — [E-Mail Settings]. % For information on the default administrator password, refer to the User’s Guide CD/DVD. Tap [E-Mail TX (SMTP)]. Select [ON] to enable E-mail TX (SMTP) settings and E-mail TX function. bizhub C368/C308 3-31…
-
Page 108: Configuring Administrator Information
Scan-to-Send function Enter the SMTP server address. Configuring administrator information Tap [Utility], and select [Administrator Settings] — [Administrator/Machine Settings] — [Administrator Reg- istration]. Enter the required information, then tap [OK]. 3-32 bizhub C368/C308…
-
Page 109: Sending The Original
Scan-to-Send function Sending the original Load the original. Tap [Scan/Fax]. Enter a destination. bizhub C368/C308 3-33…
-
Page 110
Select the type of the file to save scanned data. [Scan Size] Specify the size of the original to be scanned. [File Name/Subject Change the file name or the subject of an E-mail to be sent. Name/Other] Press the Start key. 3-34 bizhub C368/C308… -
Page 111: Fax Function
The following describes a flow to send a fax. For details, refer to page 3-39. Loading the original Entering a destination % Enter the destination fax number, and check the settings such as the image quality. Press the Start key. % Press the Start key to send the original. bizhub C368/C308 3-35…
-
Page 112: Checking The Cable Connection
Fax function Checking the cable connection Check that a modular cable is connected to the LINE port of this ma- chine. 3-36 bizhub C368/C308…
-
Page 113: Registering Transmission Information
% For information on the default administrator password, refer to the User’s Guide CD/DVD. Enter the sender information, then tap [OK]. • Sender settings • Sender Fax No. Settings Enter the name to be displayed as a sender. Enter the fax number to be displayed as a sender. bizhub C368/C308 3-37…
-
Page 114: Selecting The Dialing Method
If you do not know the type of the dialing method, operate push buttons of your phone. When you hear «beep boop beep», set [Dialing Method] to [PB]. If you do not hear «beep boop beep» after operating push buttons, select [10pps]. 3-38 bizhub C368/C308…
-
Page 115: Sending The Original
Fax function Sending the original Load the original. Tap [Scan/Fax]. Enter a destination. bizhub C368/C308 3-39…
-
Page 116
[Color], [File Type], and [File Name/Subject Name/Other] are not available when sending to a fax num- ber. Settings Description [Simplex/Duplex] Select whether to scan one or both sides of the original. [Resolution] Specify the scanning resolution. [Scan Size] Specify the size of the original to be scanned. Press the Start key. 3-40 bizhub C368/C308… -
Page 117: Sending A Fax Directly From A Pc (Pc-Fax Tx)
% Create data to be sent using application software. Configuring the fax driver % Select a fax driver, and change the setting if necessary. Entering a destination to send data % Enter a destination to send data. bizhub C368/C308 3-41…
-
Page 118: Checking The Cable Connection
If no IP address is displayed, you need to configure the network. Tap [Utility], and select [Administrator Settings] — [Network Settings] — [TCP/IP Settings]. Configure the required settings to suit your environ- ment. For details, refer to the User’s Guide CD/DVD. 3-42 bizhub C368/C308…
-
Page 119: Installing The Fax Driver
Click [Printer Install]. Proceed with the procedure according to the on-screen instructions. Printers and MFPs connected to the network are automatically searched for. Select this machine from the list. Select a fax driver. Click [Install]. Click [Finish]. bizhub C368/C308 3-43…
-
Page 120: Sending Data
Enter the destination [Name] and [FAX Number]. % To send data to more than one destination, repeat this step. % Clicking [Add from Address Book] can retrieve the registered destinations of this machine. Click [OK]. 3-44 bizhub C368/C308…
-
Page 121: Copy Function
If user authentication is enabled, the login screen appears. Tap the entry area or keyboard icon to enter the required information, then tap [Login] or press Access key. % If IC card or biometric authentication is enabled, refer to page 3-47. Load the original. Tap [Copy]. bizhub C368/C308 3-45…
-
Page 122
Specify the zoom ratio. [Duplex/Combine] Specify double-sided copying or combine copying. [Finishing] Configure the offset, punch, or staple setting for output paper. [Density] Adjust the copy density. Tap the input area for entering the number of copies. 3-46 bizhub C368/C308… -
Page 123: User Authentication
If IC card or NFC authentication is enabled, pass or place the IC card or Android terminal over or on the card reader of the authentication unit. If biometric authentication is enabled, put your finger on the finger vein reader of the authentication unit. bizhub C368/C308 3-47…
-
Page 124: Registering A Destination
Using the Control Panel to register an address book — Registration from Util- Select a destination type, and register destination information. Tap [Utility], and select [One-Touch/ User Box Reg.] — [Create One-Touch Destination] — [Address Book (Public)]. Select the type of the destination you want to register. Tap [New]. 3-48 bizhub C368/C308…
-
Page 125
] to switch setting screens while entering the required items. For information on entry items, refer to page 3-53. Enter the fax number. % Tap [Display Keypad] to display the Keypad, and enter the fax number. Tap [Close]. bizhub C368/C308 3-49… -
Page 126: Using The Control Panel To Register An Address Book — Registration In Scan/Fax Mode
Using the Control Panel to register an address book — Registration in scan/fax mode Select a destination type, and register destination information. Display the scan/fax screen. Tap [Address Reg.]. Tap [Input New Address]. Select a destination type. 3-50 bizhub C368/C308…
-
Page 127
To register the destination, tap [Address Reg.] after entering the destination using direct input, and then select the destination. What is an index? This is used as an index of a registered destination. Tap the Index key to narrow down a target desti- nation. bizhub C368/C308 3-51… -
Page 128: Using A Computer To Register A One-Touch Destination
% If the login screen appears, enter the required items, then click [Login]. Select [Store Address] and click [New Registration]. Select the type of the destination you want to register. Enter the required information such as the name, fax number, and index. 3-52 bizhub C368/C308…
-
Page 129: Information Required To Register A Destination
Enter the user ID required to log in with WebDAV. [Password] Enter the password required to log in with Web- DAV. [Host Address] Enter the address of the WebDAV server. [File Path] Enter the directory to be used as the destination. bizhub C368/C308 3-53…
-
Page 130: Registering A Group
% Tap [Name], and enter the destination name using the displayed keyboard. % For [Sort Character], enter the same name as [Name]. % This sets the appropriate index for the name, which you entered into [Name], to [Index]. To change the setting, tap [Index]. 3-54 bizhub C368/C308…
-
Page 131
% [Index]: Searches for the target destination name using an index. % [Registration Number]: Searches for the target destination using a registration number. Repeat Step 4 until you select all address books to be grouped. bizhub C368/C308 3-55… -
Page 132: Retrieving A Registered Destination
Retrieve an address book or group to specify it as a destination to which data is sent. Retrieving a destination Tap [Scan/Fax]. The destinations, which are categorized into [Favorite] when registering indexes, are displayed on the basic screen. 3-56 bizhub C368/C308…
-
Page 133
Registering a destination Narrow down destinations using index and address type. bizhub C368/C308 3-57… -
Page 134: Specifying A Destination
Retrieves destination candidates by the prefix search function using the name (registered destination name) or address (fax number, E-mail ad- dress, or computer name). This function is convenient when there are too many registered destinations. Reference For details, refer to the User’s Guide CD/DVD. 3-58 bizhub C368/C308…
-
Page 135: Using A Usb Memory Device
Connect a USB memory device to this machine. NOTICE Use the USB connector on the side that is near the Control Panel. Do not use a USB device other than a flash-memory device. Tap [Print a document from External Memory.]. bizhub C368/C308 3-59…
-
Page 136
Using a USB memory device Select data to be printed, and tap [Print]. Check print settings. 3-60 bizhub C368/C308… -
Page 137: Saving The Scanned Data In The Usb Memory Device (External Memory)
Available USB memory device Compatible with USB version 2.0/1.1 interface Formatted in FAT32 Without security function added, or with security function that can be turned off as required There is no upper limit for the memory size. bizhub C368/C308 3-61…
-
Page 138: Specifying Functions To Be Permitted For External Memory
Tap [Utility], and select [Administrator Settings] — [System Settings] — [User Box Settings]. % For information on the default administrator password, refer to the User’s Guide CD/DVD. Tap [External Memory Functional Settings]. Select [Save Document] and [ON]. Tap [OK]. 3-62 bizhub C368/C308…
-
Page 139: Saving Data In The Usb Memory Device
Connect a USB memory device to this machine. NOTICE Use the USB connector on the side that is near the Control Panel. Do not use a USB device other than a flash-memory device. Tap [Save a document to External Memory.]. bizhub C368/C308 3-63…
-
Page 140
[Color] Select whether to scan the original in color or black and white mode. [File Type] Select the type of the file to save scanned data. [Scan Size] Specify the size of the original to be scanned. 3-64 bizhub C368/C308… -
Page 141
Using a USB memory device Press the Start key. NOTICE Do not disconnect the USB memory device during data saving. bizhub C368/C308 3-65… -
Page 142: Using The Guidance Function
If you have any questions during operation, try to use this guidance function. Getting help on the currently displayed screen: Select [Function] on the Help Menu to display the guidance screen. Press the Guidance key (default: Register key 2). Select a menu. 3-66 bizhub C368/C308…
-
Page 143
Using the guidance function Narrow down the information you want to know. bizhub C368/C308 3-67… -
Page 144: Getting Help On The Desired Function Or Procedure
Returns to the preceding screen. Getting help on the desired function or procedure: Open the Help Menu, and select a menu depending on an objective to display the guidance screen. Press the Guidance key (default: Register key 2). Select a menu. 3-68 bizhub C368/C308…
-
Page 145
Using the guidance function Narrow down the information you want to know. bizhub C368/C308 3-69… -
Page 146: Help Menu List
[Service/Admin. Information] Tap this button to display the service or administrator information, ad- ministrator name, extension number, and E-mail address. [Consumables Replace/ Pro- Tap this button to check the consumables replacement or punch scrap- cessing Procedure] ping procedure. 3-70 bizhub C368/C308…
-
Page 147: Using The [Quick Security] Function
[PSWC Setting] Select whether to use Web Connection. [Security Warning Display Select whether to display the security warning screen if the admin- Setting] istrator password remains set to the default or if password rules are not satisfied. bizhub C368/C308 3-71…
-
Page 148
To display the key, tap [Utility], and select [Administrator Settings] — [System Set- tings] — [Custom Display Settings] — [Main Menu Default Settings] — [Main Menu Key]. For information on the default administrator password, refer to the User’s Guide CD/DVD. Reference For details, refer to the User’s Guide CD/DVD. 3-72 bizhub C368/C308… -
Page 149: Advanced Functions
Advanced Functions…
-
Page 151: Using Advanced Functions
You can use the address book for personal use (My Address Book). • This requires the association with My Panel Manager. In addition, this machine supports advanced functions such as the barcode font, unicode font, and OCR font. bizhub C368/C308…
-
Page 152: Association With Application
% Enter the license code to enable the function. For details, refer to page 4-9. Configuring each function (Administrator) % Configure the required settings for each advanced function. For details, refer to page 4-11. Reference For details on the procedure, refer to the User’s Guide CD/DVD. bizhub C368/C308…
-
Page 153: Enabling The I-Option Function
% For information on the default administrator password, refer to the User’s Guide CD/DVD. Enter the token number shown in the token certificate. Select [Yes], then tap [OK]. This machine is connected to the Internet to communicate with the License Management Server (LMS), and it restarts automatically. bizhub C368/C308…
-
Page 154: Registering The I-Option License
% For information on the default administrator password, refer to the User’s Guide CD/DVD. Tap [Yes] and [OK]. Tapping [Print] prints the serial number and request code. % Prepare at hand the printed serial number, request code, and token certificate supplied with i-Op- tion. bizhub C368/C308…
-
Page 155
Code], then click [Next]. % The URL is https://lms.konicaminolta.com/index.aspx. Enter the [Token Number], select the option you want to register from the [Product Description] list, then click [Next]. Confirm the registration contents, then click [Generate License Code]. bizhub C368/C308… -
Page 156
You could also store them in your USB memory device. The license code input could be omitted by using a USB memory device to achieve a convenient operation. When using a USB memory device, insert the USB memory device and click [Download] to store the license code. bizhub C368/C308… -
Page 157: Enabling The I-Option Function Using The License
Tap [Utility], and select [Administrator Settings] — [Forward] — [License Settings] — [Install License] — [Function/Licence Code]. % For information on the default administrator password, refer to the User’s Guide CD/DVD. Enter the license and function codes you wrote down. Select [Yes], then tap [OK]. This machine restarts automatically. bizhub C368/C308…
-
Page 158
By using a USB memory device Connect the USB memory device stored with the license code. Tap [Utility], and select [Administrator Settings] — [Forward] — [License Settings] — [Install License from Ext. Memory]. Select [Yes], then tap [OK]. This machine restarts automatically. 4-10 bizhub C368/C308… -
Page 159: Configuring Each Function
Using advanced functions Configuring each function Configure the required settings for each advanced function. Reference For details on the required setting items for each advanced function, refer to the User’s Guide CD/DVD. bizhub C368/C308 4-11…
-
Page 160: Using The Web Browser Function
% For details, refer to page 4-19. Displaying Web pages % For details, refer to page 4-20. Printing the currently displayed page or the linked file % For details, refer to page 4-20. Reference For details, refer to the User’s Guide CD/DVD. 4-12 bizhub C368/C308…
-
Page 161: Enabling The Web Browser Function
% For information on the default administrator password, refer to the User’s Guide CD/DVD. Select [ON], then tap [OK]. This machine is connected to the Internet to communicate with the License Management Server (LMS), and it restarts automatically. bizhub C368/C308 4-13…
-
Page 162: Registering The License
Display the serial number of this machine. Tap [Utility], and select [Device Information]. Write down the serial number of this machine. Access the Web site of the License Management Server (LMS). Enter the [MFP Serial Number], then click [Next]. % The URL is https://lms.konicaminolta.com/activate. 4-14 bizhub C368/C308…
-
Page 163
You could also store them in your USB memory device. The license code input could be omitted by using a USB memory device to achieve a convenient operation. When using a USB memory device, insert the USB memory device and click [Download] to store the license code. bizhub C368/C308 4-15… -
Page 164: Enabling The Web Browser Using The License
Tap [Utility], and select [Administrator Settings] — [Network Settings] — [Forward] (twice) — [Web Browser Settings] — [Web Browser Usage Settings]. % For information on the default administrator password, refer to the User’s Guide CD/DVD. Select [ON], then tap [OK]. When the screen shown below appears, tap [Function/License Code]. 4-16 bizhub C368/C308…
-
Page 165
Enter the license code you wrote down. Select [Yes], then tap [OK]. This machine restarts automatically. By using a USB memory device Tap [Utility], and select [Administrator Settings] — [Network Settings] — [Forward] (twice) — [Web Browser Settings] — [Web Browser Usage Settings]. bizhub C368/C308 4-17… -
Page 166
Using the Web browser function Select [ON], then tap [OK]. Wait a few moments until the screen shown below appears. Connect the USB memory device stored with the license code. 4-18 bizhub C368/C308… -
Page 167: Starting The Web Browser
Using the Web browser function Select [Install License from Ext. Memory]. Select [Yes] , then tap [OK]. This machine restarts automatically. Starting the Web browser Tap [Web Browser]. The Web browser starts. Tips The pre-specified home page appears. bizhub C368/C308 4-19…
-
Page 168: Displaying Web Pages
[Simplex/Duplex] Select whether to print one side or both sides of sheets of paper. To specify 2-sided printing, select the binding position. [Finishing] Configure the offset, punch, or staple setting for output paper. Press the Start key. 4-20 bizhub C368/C308…
-
Page 169
[Simplex/Duplex] Select whether to print one side or both sides of sheets of paper. To specify 2-sided printing, select the binding position. [Finishing] Configure the offset, punch, or staple setting for output paper. Press the Start key. bizhub C368/C308 4-21… -
Page 170
Using the Web browser function 4-22 bizhub C368/C308… -
Page 171: Troubleshooting
Troubleshooting…
-
Page 173: Main Messages And Remedies
For Waste Toner Box: When the message [Waste Toner Box needs to be replaced.] appears, replace it based on the maintenance contract. Contact your service representative if the messages continue to appear even after replacement or cleaning has been carried out. bizhub C368/C308…
-
Page 174: When A Paper Jam Message Persists
If a defective part can be separated in order to be able to continue operations after a problem has been de- tected, [Continue] or [Recover Data] is displayed. To continue operations, select any key. However, the prob- lem has not been resolved, so contact your service representative immediately. bizhub C368/C308…
-
Page 175: When [Stabilizing Image.] Appears
In case image stabilization does not finish after a short while, contact your service representative. NOTICE You cannot interrupt or prohibit image stabilization. Reference To perform image stabilization on a voluntary basis, refer to the User’s Guide CD/DVD. bizhub C368/C308…
-
Page 176: When Printing Quality Has Deteriorated
Printing quality deteriorates if the Print Head Glass is dirty. If this occurs, clean the Print Head Glass ac- cording to the following procedure. Open the Front Door of the machine. Release the Waste Toner Box Lock Lever, then remove the Waste Toner Box. Remove the Printhead Cleaner from the Front Door of this machine. bizhub C368/C308…
-
Page 177
% Repeat this operation approximately three times for all of the Print Head Glass sections. Mount the Printhead Cleaner onto the Front Door of this machine. Install the Waste Toner Box. Close the Front Door of the machine. bizhub C368/C308… -
Page 178: When The Machine Cannot Be Powered On
Check whether the power plug of this machine is firmly plugged into the power outlet. Also check that the breaker has not tripped. Check to see that the Main Power Switch and the Power key are turned ON. In case the machine cannot be powered on even after checking, contact your service representative. bizhub C368/C308…
-
Page 179: When The Touch Panel Is Not Visible
Auto Power OFF mode, press the Power key to display the Touch Panel. To use it outside the preset operating hours, follow the on-screen instructions. Check to see that the Main Power Switch and the Power key are turned ON. In case the Touch Panel does not appear even after checking it, contact your service representative. bizhub C368/C308…
-
Page 180: When A Message Appears To Replace Consumables Or Carry Out Cleaning
When the punch scrap box is full When the punch scrap box is full, a message appears to prompt you to dispose of the punch scraps (at re- placement by user). Take action while referring to the label inside the machine. 5-10 bizhub C368/C308…
-
Page 181: When Toner Is Running Out In The Toner Cartridge
Do not replace a Toner Cartridge of a color that is not displayed. When it is time to replace a Toner Cartridge of a color other than black, printing can be forcibly con- tinued using black. Tap [Continue], and then select a desired print job. bizhub C368/C308 5-11…
-
Page 182: When It Is Time To Replace A Drum Unit
For details, contact your service representative. When it is time to replace a Developing Unit of a color other than black, printing can be forcibly con- tinued using black. Tap [Continue], and then select a desired print job. 5-12 bizhub C368/C308…
-
Page 183: When A Waste Toner Box Is Full
When a Waste Toner Box is full When the Waste Toner Box is full, a message appears to prompt you to replace it (at replacement by user). Tap [Start Guidance], then follow the displayed guidance to take an action. bizhub C368/C308 5-13…
-
Page 184: Replacing A Toner Cartridge
If you get toner into your eyes, immediately rinse them with running water for over 15 minutes. Seek medical advice if irritation persists. If you swallow toner, rinse out your mouth and drink a few glasses of water. Seek medical advice if nec- essary. 5-14 bizhub C368/C308…
-
Page 185: Replacing A Waste Toner Box
7WARNING Do not throw toner or a container that contains toner (e.g., Toner Cartridge and Developing Unit) into an open flame. The hot toner may scatter and cause burns or other damage. bizhub C368/C308 5-15…
-
Page 186
If you get toner into your eyes, immediately rinse them with running water for over 15 minutes. Seek medical advice if irritation persists. If you swallow toner, rinse out your mouth and drink a few glasses of water. Seek medical advice if nec- essary. 5-16 bizhub C368/C308… -
Page 187: Replacing A Drum Unit
Tap [Continue], and then select a desired print job. After replacing a Drum Unit, be sure to clean the Print Head Glass for each color. For details on how to clean the Print Head Glass, refer to page 5-6. bizhub C368/C308 5-17…
-
Page 188
When a message appears to replace consumables or carry out cleaning 5-18 bizhub C368/C308… -
Page 189: Index
Index…
-
Page 191: Index By Item
Job 2-32 User authentication 3-47 Keypad 2-30 Web Browser 4-12 License Management Server (LMS) 4-6 4-14 Loading Paper 2-33 2-34 2-35 2-36 XPS 3-6 Low Power mode 2-21 Main Menu 2-24 MFP 2-12 Multi-job 2-32 Options 2-8 2-14 bizhub C368/C308…
-
Page 192
Index by item bizhub C368/C308…

User’s Guide
Security Operations
2017. 2 Ver. 1.01

Contents
1Security
|
1.1 |
Introduction ……………………………………………………………………………………………………………………. |
1-2 |
|
Administrators…………………………………………………………………………………………………………………… |
1-2 |
|
|
Compliance with the ISO15408 Standard …………………………………………………………………………….. |
1-2 |
|
|
Operating Precautions ……………………………………………………………………………………………………….. |
1-2 |
|
|
INSTALLATION CHECKLIST……………………………………………………………………………………………….. |
1-4 |
|
|
1.2 |
Security Functions ………………………………………………………………………………………………………….. |
1-7 |
|
Check Count Clear Conditions ……………………………………………………………………………………………. |
1-7 |
|
|
1.3 |
Precautions for Operation Control…………………………………………………………………………………… |
1-9 |
|
Roles of the Owner of the Machine ……………………………………………………………………………………… |
1-9 |
|
|
Roles and Requirements of the Administrator……………………………………………………………………….. |
1-9 |
|
|
Password Usage Requirements ………………………………………………………………………………………….. |
1-9 |
|
|
External authentication server control requirements …………………………………………………………….. |
1-10 |
|
|
Security function operation setting operating requirements…………………………………………………… |
1-10 |
|
|
Operation and control of the machine ………………………………………………………………………………… |
1-10 |
|
|
Machine Maintenance Control…………………………………………………………………………………………… |
1-12 |
|
|
Precautions for using the printer driver……………………………………………………………………………….. |
1-12 |
|
|
1.4 |
Miscellaneous……………………………………………………………………………………………………………….. |
1-13 |
|
Password Rules ………………………………………………………………………………………………………………. |
1-13 |
|
|
Precautions for Use of Various Types of Applications…………………………………………………………… |
1-14 |
|
|
Encrypting communications ……………………………………………………………………………………………… |
1-14 |
|
|
IPsec setting …………………………………………………………………………………………………………………… |
1-14 |
|
|
Print functions…………………………………………………………………………………………………………………. |
1-15 |
|
|
IPP printing …………………………………………………………………………………………………………………….. |
1-15 |
|
|
Items of Data Cleared by Overwrite All Data Function ………………………………………………………….. |
1-16 |
|
|
Fax functions…………………………………………………………………………………………………………………… |
1-16 |
|
|
USB keyboard…………………………………………………………………………………………………………………. |
1-16 |
|
|
Different types of boxes……………………………………………………………………………………………………. |
1-17 |
|
|
Hardware and software used in the machine ………………………………………………………………………. |
1-17 |
|
|
Firmware integrity verification function ……………………………………………………………………………….. |
1-17 |
|
|
CS Remote Care function …………………………………………………………………………………………………. |
1-18 |
|
|
Terminating a Session and Logging out ……………………………………………………………………………… |
1-18 |
|
|
Authentication error during external server authentication…………………………………………………….. |
1-18 |
2Administrator Operations
|
2.1 |
Accessing the Administrator Mode……………………………………………………………………………….. |
… 2-2 |
|
2.1.1 |
Accessing the Administrator Mode………………………………………………………………………………………. |
2-2 |
|
2.1.2 |
Accessing the User Mode…………………………………………………………………………………………………… |
2-8 |
|
2.2 |
Enhancing the Security Function……………………………………………………………………………………. |
2-12 |
|
2.2.1 |
Items cleared by HDD Format …………………………………………………………………………………………… |
2-14 |
|
2.2.2 |
Setting the Password Rules………………………………………………………………………………………………. |
2-15 |
|
2.2.3 |
Setting the Enhanced Security Mode …………………………………………………………………………………. |
2-17 |
|
2.3 |
Protecting Machine from Illegal Firmware Update………………………………………………………….. |
2-20 |
|
Setting the FW Update (USB) Password …………………………………………………………………………….. |
2-20 |
|
|
2.4 |
Preventing Unauthorized Access …………………………………………………………………………………… |
2-23 |
|
Setting Prohibited Functions When Authentication Error ………………………………………………………. |
2-23 |
|
|
2.5 |
Canceling the Operation Prohibited State………………………………………………………………………. |
2-25 |
|
Performing Release Setting ………………………………………………………………………………………………. |
2-25 |
|
|
2.6 |
Setting the Authentication Method ………………………………………………………………………………… |
2-27 |
|
2.6.1 |
Setting the Authentication Method …………………………………………………………………………………….. |
2-27 |
|
2.6.2 |
Setting the External Server ……………………………………………………………………………………………….. |
2-30 |
|
2.7 |
ID & Print Setting Function…………………………………………………………………………………………….. |
2-32 |
|
Setting ID & Print……………………………………………………………………………………………………………… |
2-32 |
|
bizhub 368/308 |
Contents-1 |

|
2.8 |
……………………………………………………………………………..ID & Print Operation Setting Function |
2-34 |
|
Making ID & Print Operation Setting…………………………………………………………………………………… |
2-34 |
|
|
2.9 |
Auth. Operation Setting when print Documents are Stored Function ………………………………. |
2-35 |
|
Setting Auth. Operation Setting when print Documents are Stored Function…………………………… |
2-35 |
|
|
2.10 |
System Auto Reset Function …………………………………………………………………………………………. |
2-36 |
|
Setting the System Auto Reset function……………………………………………………………………………… |
2-36 |
|
|
2.11 |
User Setting Function……………………………………………………………………………………………………. |
2-38 |
|
Making user setting………………………………………………………………………………………………………….. |
2-39 |
|
|
2.12 |
Account Track Setting Function…………………………………………………………………………………….. |
2-44 |
|
Making account setting…………………………………………………………………………………………………….. |
2-44 |
|
|
2.13 |
User Box Function ………………………………………………………………………………………………………… |
2-49 |
|
2.13.1 |
Setting the User Box………………………………………………………………………………………………………… |
2-49 |
|
2.13.2 |
Changing the user/account attributes and box password …………………………………………………….. |
2-54 |
|
2.13.3 |
Setting Memory RX………………………………………………………………………………………………………….. |
2-59 |
|
2.14 |
Changing the Administrator Password…………………………………………………………………………… |
2-62 |
|
Changing the Administrator Password ……………………………………………………………………………….. |
2-62 |
|
|
2.15 |
Protecting Data in the HDD……………………………………………………………………………………………. |
2-65 |
|
2.15.1 |
Setting the Encryption Key (encryption word) ……………………………………………………………………… |
2-65 |
|
2.15.2 |
Changing the Encryption Key ……………………………………………………………………………………………. |
2-69 |
|
2.15.3 |
Setting the Overwrite HDD Data ………………………………………………………………………………………… |
2-71 |
|
2.16 |
Overwrite All Data Function …………………………………………………………………………………………… |
2-73 |
|
Setting the Overwrite All Data function……………………………………………………………………………….. |
2-73 |
|
|
2.17 |
Obtaining Job Log…………………………………………………………………………………………………………. |
2-75 |
|
2.17.1 |
Obtaining and deleting a Job Log………………………………………………………………………………………. |
2-75 |
|
2.17.2 |
Downloading the Job Log data………………………………………………………………………………………….. |
2-77 |
|
Job Log data…………………………………………………………………………………………………………………… |
2-79 |
|
|
2.18 |
Setting time/date in machine…………………………………………………………………………………………. |
2-88 |
|
2.18.1 |
Setting time/date……………………………………………………………………………………………………………… |
2-88 |
|
2.18.2 |
Setting daylight saving time………………………………………………………………………………………………. |
2-91 |
|
2.19 |
SSL Setting Function …………………………………………………………………………………………………….. |
2-93 |
|
2.19.1 |
Device Certificate Setting …………………………………………………………………………………………………. |
2-93 |
|
2.19.2 |
SSL Setting …………………………………………………………………………………………………………………….. |
2-95 |
|
2.19.3 |
Removing a Certificate……………………………………………………………………………………………………… |
2-96 |
|
2.20 |
TCP/IP Setting Function………………………………………………………………………………………………… |
2-97 |
|
2.20.1 |
Setting the IP Address ……………………………………………………………………………………………………… |
2-97 |
|
2.20.2 |
Registering the DNS Server ………………………………………………………………………………………………. |
2-98 |
|
2.21 |
E-Mail Setting Function …………………………………………………………………………………………………. |
2-99 |
|
Setting the SMTP Server (E-Mail Server) …………………………………………………………………………….. |
2-99 |
3User Operations
|
3.1 |
User Authentication Function ………………………………………………………………………………………….. |
3-2 |
|
3.1.1 |
Performing user authentication……………………………………………………………………………………………. |
3-2 |
|
3.1.2 |
Accessing the ID & Print Document……………………………………………………………………………………… |
3-6 |
|
3.2 |
Change Password Function…………………………………………………………………………………………….. |
3-7 |
|
Performing Change Password …………………………………………………………………………………………….. |
3-7 |
|
|
3.3 |
Secure Print Function ……………………………………………………………………………………………………. |
3-10 |
|
Accessing the Secure Print Document ……………………………………………………………………………….. |
3-10 |
|
|
3.4 |
User Box Function ………………………………………………………………………………………………………… |
3-13 |
|
3.4.1 |
Setting the User Box………………………………………………………………………………………………………… |
3-13 |
|
3.4.2 |
Changing the user/account attributes and box password …………………………………………………….. |
3-18 |
|
3.4.3 |
Accessing the User Box and User Box file ………………………………………………………………………….. |
3-24 |
|
bizhub 368/308 |
Contents-2 |

4Application Software
|
4.1 |
Data Administrator………………………………………………………………………………………………………….. |
4-2 |
|
4.1.1 |
Accessing from Data Administrator ……………………………………………………………………………………… |
4-2 |
|
4.1.2 |
Setting the user authentication method………………………………………………………………………………… |
4-5 |
|
4.1.3 |
Changing the authentication mode………………………………………………………………………………………. |
4-6 |
|
4.1.4 |
Making the user settings…………………………………………………………………………………………………….. |
4-8 |
|
4.1.5 |
Making the account settings……………………………………………………………………………………………….. |
4-9 |
|
4.1.6 |
DNS Server Setting Function …………………………………………………………………………………………….. |
4-10 |
|
4.1.7 |
E-Mail Setting Function…………………………………………………………………………………………………….. |
4-11 |
|
bizhub 368/308 |
Contents-3 |


|
1.1 |
Introduction |
1 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
1Security
1.1Introduction
Thank you for purchasing our product.
This User’s Guide contains the operating procedures and precautions to be used when using the security functions offered by the bizhub 368/308 machine. To ensure the best possible performance and effective use of the machine, read this manual thoroughly before using the security functions. The administrator of the machine should keep this manual for ready reference. The manual should be of great help in finding solutions to operating problems and questions.
This User’s Guide (version 1.01) covers the following.
|
Model name |
bizhub 368/bizhub 308 |
|
Version |
G00-09 |
Administrators
<Administrator of the machine>
There are two types of administrators; one who is implemented on the machine in advance, and the other who is registered by the implemented administrator. The former is called the built-in administrator and the latter is called a user administrator. Below, the administrator of the machine means the build-in administrator.
<User administrator>
The user administrator is a user who is given the authority to operate the machine as an administrator. The administrator of the machine or the user administrator can register the user administrator. Be sure that «Precautions for Operation Control» applies to the user administrator. For details, see page 1-9.
The differences from the administrator of the machine are as follows:
—The same procedure as a user applies to the user administrator when he or she changes the password or fails authentication.
—To change password, log on to the User Mode.
<Note>
Below, the administrator collectively means both the administrator of the machine and the user administrator.
Compliance with the ISO15408 Standard
When the Enhanced Security Mode on this machine is set to [ON], more enhanced security functions are available.
This machine offers the security functions that comply with the ISO/IEC15408 (level: EAL2) and U.S. Government Approved Protection Profile — U.S. Government Protection Profile for Hardcopy Devices Version 1.0 (IEEE Std 2600.2TM-2009).
Operating Precautions
The machine gives an alarm message or an alarm sound (peep) when a wrong operation is performed or a wrong entry is made during operation of the machine. (No «peep» alarm sound is issued if a specific sound setting in Sound Setting of Accessibility Setting is set to [OFF].) If the alarm message or alarm sound is given, perform the correct operation or make the correct entry according to the instructions given by the message or other means.
The administrator must not leave the machine with each setting screen left displayed before, during, and after access to each mode. If he or she has to leave the machine, make sure that he or she logs out and returns the screen to the authentication screen.
The administrator must make sure that each individual general user logs out and returns the screen to the authentication screen if he or she leaves the machine with each mode screen left displayed before, during, and after access to each mode.

If an error message appears during operation of the machine, perform steps as instructed by the message. For details of the error messages, refer to the User’s Guide furnished with the machine. If the error cannot be remedied, contact your service representative.
Page rotation in the preview during scanning of the document in each of the copying, E-mail, and fax functions provided by the machine is reflected in the output. In the E-mail and fax functions, data can be deleted by the page and the deletion is reflected in the output.
The Web Connection functions can be used only if the setting is made to accept «Cookie.»
For any query, request, or opinion concerning the machine, please contact your dealer from which you purchased your machine or Service Representative.
Any notice concerning this machine will be given in writing by the dealer from which you purchased your machine or Service Representative.
INSTALLATION CHECKLIST
This Installation Checklist contains items that are to be check by the Service Engineer installing this machine. The Service Engineer should check the following items, then explain each checked item to the administrator of the machine.
To Service Engineer
Make sure that each of these items is properly carried out by checking the box on the right of each item.
1.Perform the following steps before installing this machine.
Check with the administrator of the machine to determine if the security functions of this machine should be enhanced. If the functions should be enhanced, check the following. If the security functions are not to be enhanced, quit the operation without checking the following.
Before installing the machine, check with the administrator of the machine to determine if the following is confirmed.
•Whether the Service Engineer has been informed that the unpacking procedure is to be performed by the Service Engineer in the presence of the administrator.
•Whether the machine has been under the control of the administrator of the machine with a check made to ensure that evidently the machine has not been unpacked or
used.
The Service Engineer should obtain the administrator’s consent to the performance of this item.
If the machine has been unpacked, check with the administrator that it was the administrator who unpacked the machine and nobody but the administrator has gain access to the machine after the unpacking. Then, obtain the administrator’s consent to the performance of the installation procedure for the unpacked machine before attempting to start the procedure. If the administrator’s consent cannot be obtained, call the dealer.
I swear that I would never disclose information as it relates to the settings of this machine to anybody, or perform malicious or intentional act during setup and service procedures for the machine.
When giving a copy of the User’s Guide, explain the following to the administrator:
•A digital signature is assigned to the data certified by ISO15408. To ensure integrity of the file, have the administrator of the machine confirm the digital signature using the property of the provided data file in the user’s PC environment.
Confirm the digital signature as follows.
Right click the provided exe file to display the property screen.
Select [Digital Signatures] — [Details] — [General], and check that Konica Minolta, Inc. is displayed in the Name of signer field.
Select [View Certificate] — [General]. Then, check that the signing time is within the validated date of the certificate and that the certificate has been issued by a reliable certification authority.
Write down the serial number shown in [View Certificate] — [Details]. Access to the URL for CRL Distribution Points and confirm that the serial number is not shown in [Revocation List]. For confirmation, the Internet environment is required.
•Two versions are available, the HTML version and User’s Guide Security Operations (this User’s Guide).
•In HTML version, option settings are described including functions those can be universally configured, but it does not mean that all of them are available.
•This User’s Guide must first be read and the conditions described in this User’s Guide take precedence over the HTML version.
•If the security functions of the machine are to be enhanced, the machine and its surrounding environment should be set up and operated according to this User’s Guide.
Refer to the Service Manual and perform the required installation and setup steps. During the installation and setup procedure, make sure that no unnecessary parts are mounted on the machine and have the administrator of the machine confirm that no unnecessary parts are mounted on the machine.
•Explain to the administrator making him/her check the cover of the Service Manual to
be referred that it is for bizhub 368/bizhub 308 (Version: G00-09).
Explain to the administrator that the following settings must be performed referring to the manuals above.
•The Service Engineer must have the administrator confirm that the digital signature is assigned to the firmware and the version of the firmware to be updated is the one that is written on the Service Manual.

2.After this machine is installed, refer to the Service Manual and perform the following steps.
Check that the model name and the Firmware version (card version) checked with the Service Manual agree with the value shown on the Firmware version display screen.
Check also that the MFP model name and the part numbers of the MFP board and the eMMC board agree with those described in the Service Manual.
If there is a mismatch in the Firmware version number, explain to the administrator of the machine that upgrading of the Firmware is necessary and perform upgrading of the Firmware.
Check that the Fax Kit has been mounted and set up properly, if fax functions are to be used.
After the installation, conduct transmission and reception tests to make sure that the Fax Kit has been mounted and set up properly.
Let the machine read the Custom Function Pattern Selection setting file to which an electronic signature is assigned.
Explain to the administrator that the Custom Function Pattern Selection setting file is dedicated to the machine in question.
Get the administrator of the machine to confirm that [ISO15408] is selected for [Send/Save] of [Custom Function Pattern Selection] in the Administrator Settings and obtain his or her consent not to change the setting.
Set CE Authentication to [ON] and set the CE Password.
Make the service settings necessary for the Enhanced Security Mode.
3.After this machine is installed, refer to this User’s Guide and perform the following steps.
Check that the Administrator Password has been set by the administrator of the machine. Select [Restrict] when the confirmation screen of machine usage information is displayed.
If [Allow] is mistakenly selected, make the following settings:
•Set the function counter (Transmission Meter Count and Device Information) to [Restrict].
• Set the TX Operation Log setting to [Do not Save].
For the setting procedure, see bizhub 558/458/368/308 User’s Guide version 1.00 A9HJ- 9590BA-00.
Setting by the Service Engineer is required for the following:
•Debug Log Collection System function (software SW No. 155)
•Export Debug Log
Check that the Encryption Key has been set by the administrator of the machine.
Check that the Overwrite HDD Data has been set by the administrator of the machine.
Check that User Authentication has been set to [ON (MFP)], [External Server Authentication] (Active Directory only), or [Main + External Server] (Active Directory only) by the administrator of the machine.
Check that the date and time have been correctly set in the machine by the administrator of the machine.
Check that the Job Log Settings (Audit Log) has been set to [Yes] by the administrator of the machine.
Check that the certificate for SSL communications has been registered by the administrator of the machine.
In accordance with the security policies of the organization, register the certificate that is issued by a reliable authentication authority.
Check that the ID & Print Settings has been set to [ON] by the administrator of the machine.
Check that the Memory RX Setting has been set to [Yes] by the administrator of the machine.
Check that IPsec has been set by the administrator of the machine for communications between the machine and the external authentication server.
Check that IPsec has been set by the administrator of the machine for communications between the machine and the DNS server.
Check that IPsec has been set by the administrator of the machine for communications between the machine and the SMTP server.
Check that IPsec has been set by the administrator of the machine for communications between the machine and a client PC.

Let the administrator of the machine set Enhanced Security Mode to [ON].
Check that the FW Update (USB) Password has been set by the administrator of the machine.
Check that the various functions to be disabled manually have been properly disabled by the administrator of the machine.
The languages, in which the contents of the User’s Guide Security Operations have been evaluated, are Japanese and English.
The following lists the manuals compatible with bizhub 368/bizhub 308 (Version: G00-09).
•bizhub 558/458/368/308 User’s Guide Ver. 1.00 A9HJ-9590BA-00
•bizhub 368/308 User’s Guide Security Operations 2017. 2 Ver. 1.01
Explain to the administrator of the machine that the settings for the security functions for this machine have been specified.
After completing the checks, keep a copy of this list in the Service Representative and give the original of this list to the administrator of the machine.
Please direct your any queries about using the machine to the Service Representative shown below.
|
Product Name |
Company Name |
User Division Name, |
Person in charge |
|
|
Contact |
||||
|
Customer (administrator of the |
||||
|
machine) |
||||
|
Service Representative |
||||

1.2Security Functions
Setting the Enhanced Security Mode to [ON] will validate the security function of this machine. For details of the settings of different security functions to be changed by turning [ON] the Enhanced Security Mode, see page 2-12.
The following the major security functions when the Enhanced Security Mode is set to [ON].
|
Function |
Description |
|
Identification and au- |
Access control is then provided through password authentication for any ac- |
|
thentication function |
cess to the Administrator Mode, User Authentication mode, User Box, a User |
|
Box data file, and a Secure Print document. Access is thereby granted only |
|
|
to the authenticated user. A password that can be set must meet the Pass- |
|
|
word Rules. The machine does not accept setting of an easily decipherable |
|
|
password. For details of the Password Rules, see page 1-13. |
|
|
If a wrong password is entered, during password authentication, a predeter- |
|
|
mined number of times (once to three times.) or more set by the administra- |
|
|
tor, the machine determines that it is unauthorized access through Prohibited |
|
|
Functions When Authentication Error, prohibiting any further entry of the |
|
|
password. By prohibiting the password entry operation, the machine pre- |
|
|
vents unauthorized use or removal of data. The administrator is responsible |
|
|
for resetting the prohibition of the password entry operation. For details, see |
|
|
page 2-25. |
|
|
User limiting function |
Specific functions to be used by each user/account may be limited. For de- |
|
tails, see page 2-38. |
|
|
HDD encryption function |
By setting the Encryption Key, the data stored in the HDD is encrypted, there- |
|
by protecting the data in the HDD. For details, see page 2-65. |
|
|
Auditing function |
Information including operations performed on the machine and a job history |
|
can be stored in the HDD. Setting the Job Log (Audit Log) allows an illegal |
|
|
act or inadequate operation performed on the machine to be traced. The ob- |
|
|
tained Job Log can be downloaded and viewed from the Web Connection. |
|
|
For details, see page 2-75. |
|
|
Residual information de- |
When the machine is to be discarded or use of a leased machine is terminat- |
|
leting function |
ed at the end of the leasing contract, setting of the Overwrite HDD Data func- |
|
tion while the machine was in use allows residual unnecessary data to be |
|
|
deleted, because the machine overwrites a specific overwrite value over the |
|
|
unnecessary data. This prevents data leakage. (Passwords, addresses, and |
|
|
other data set while the machine was in use should, however, be deleted |
|
|
manually.) For details, see page 2-71. |
|
|
To delete data including the passwords, addresses, and other data all at |
|
|
once, the Overwrite All Data function overwrites and erases all data stored in |
|
|
all spaces of the HDD. The function also resets all passwords saved in the |
|
|
flash memory and eMMC to factory settings, preventing data from leaking. |
|
|
For details, see page 2-73. For details of items to be cleared by Overwrite All |
|
|
Data function, see page 1-16. |
|
|
Network communication |
Communication data transmitted to or from the machine and client PC can |
|
protecting function |
be encrypted using the IPsec, which prevents information leakage through |
|
sniffing over the network. For details, see page 1-14. |
|
Check Count Clear Conditions
In the Enhanced Security Mode, the number of wrong entries at the time of authentication is checked. The following is the conditions for clearing or resetting the number.
<Administrator Authentication>
—Authentication of Administrator of the machine is successful.
<User Authentication Mode>
—Authentication of User Administrator is successful.
—User Authentication mode is successful.
—Release of Prohibited Functions When Authentication Error is executed.
<Account Track Mode>
—Account Track mode is successful.
—Release of Prohibited Functions When Authentication Error is executed.

<Secure Print>
—Authentication of Secure Print is successful.
—Release of Prohibited Functions When Authentication Error is executed.
<Box>
—Authentication of User Box is successful.
—Authentication for execution of change of User Box Name and User Box Password is successful.
—Release of Prohibited Functions When Authentication Error is executed.

|
1.3 |
Precautions for Operation Control |
1 |
1.3Precautions for Operation Control
This machine and the data handled by this machine should be used in an office environment that meets the following conditions. The machine must be controlled for its operation under the following conditions to protect the data that should be protected.
Roles of the Owner of the Machine
The owner (an individual or an organization) of the machine should take full responsibility for controlling the machine, thereby ensuring that no improper operations are performed.
—The owner of the machine should have the administrator recognize the organizational security policy and procedure, educate him or her to comply with the guidance and documents prepared by the manufacturer, and allow time for him or her to acquire required ability. The owner of the machine should also operate and manage the machine so that the administrator can configure and operate the machine appropriately according to the policy and procedure.
—The owner of the machine should have users of the machine recognize the organizational security policy and procedure, educate them to follow the policy and procedure, and operate and manage the machine so that the users acquire the required ability.
—The owner of the machine should vest the user with authority to use the machine according to the organizational security policy and procedure.
—The owner of the machine should operate and manage the machine so that the administrator checks the Job Log (Audit Log) data at appropriate timing to thereby determine whether a security compromise or a faulty condition has occurred during an operating period.
—If the Job Log (Audit Log) data is to be exported to another product, the owner of the machine should ensure that only the administrator performs the task. The owner of the machine should also operate and manage the machine so that the Job Log (Audit Log) data is not illegally accessed, deleted, or altered.
Roles and Requirements of the Administrator
The administrator should take full responsibility for controlling the machine, thereby ensuring that no improper operations are performed.
—A person who is capable of taking full responsibility for controlling the machine should be appointed as the administrator to make sure that no improper operations are performed.
—When using an external authentication server, an SMTP server (mail server), or a DNS server, each server should be appropriately managed by the administrator and should be periodically checked to confirm that settings have not been changed without permission.
Password Usage Requirements
The administrator must control the Administrator Password, Encryption Key, FW Update (USB) Password, and User Box Password appropriately so that they may not be leaked. These passwords should not be ones that can be easily guessed. The user, on the other hand, should control the Secure Print Password and User Password appropriately so that they may not be leaked. Again, these passwords should not be ones that can be easily guessed.
<To Achieve Effective Security>
—Make absolutely sure that only the administrator of the machine knows the Administrator Password.
—Make absolutely sure that only the administrator knows the Encryption Key, FW Update (USB) Password, and User Box Password.
—Make sure that the administrator of the machine changes the Administrator Password regularly.
—The administrator must change the Encryption Key, FW Update (USB) Password, and User Box Password at regular intervals.
—The administrator of the machine should make sure that any number that can easily be guessed from birthdays, employee identification numbers, and the like is not set for the Administrator Password.
—The administrator should make sure that any number that can easily be guessed from birthdays, employee identification numbers, and the like is not set for the Account Password, Encryption Key, FW Update (USB) Password, and User Box Password.
—If a User Password has been changed, the administrator should have the corresponding user change the password as soon as possible.
—If the Administrator Password has been changed by the Service Engineer, the administrator of the machine should change the Administrator Password as soon as possible.

|
1.3 |
Precautions for Operation Control |
1 |
—The administrator should have users ensure that the passwords set for the User Authentication, Secure Print, and the box that can be used by the user are known only by the user concerned.
—The administrator should have users change the passwords set for the User Authentication at regular intervals.
—The administrator of the machine should have the user administrator log on to the User Mode and change his or her password in [Utility] — [User Settings] — [Change Password] if he or she changes the password.
—The administrator should make sure that any user does not set any number that can easily be guessed from birthdays, employee identification numbers, and the like for the passwords set for the User Authentication and Secure Print.
—The administrator should disclose the Account Password to the user in accordance with the operating environment of the machine and the security policies of the organization on his or her own responsibility.
External authentication server control requirements
The administrator and the server administrator are required to apply patches to, or perform account control for, this machine and the external authentication server connected to the office LAN in which the machine is installed to ensure operation control that achieves appropriate access control.
This machine can be used only after the user who uses this machine has been registered in the external authentication server. The server administrator should also check registered users at regular intervals to thereby ensure that any unnecessary users are left registered.
Security function operation setting operating requirements
The administrator should observe the following operating conditions.
—The administrator should make sure that the machine is operated with the settings described in the installation checklist made properly in advance.
—The administrator should make sure of correct operation control so that the machine is used with the Enhanced Security Mode set to [ON].
—The administrator should make sure of correct operation control so that the appropriate FW Update (USB) Password is used with [FW Update (USB) Permission Setting] set to [Password Priority].
—When the Enhanced Security Mode is turned [OFF], the administrator is to make various settings according to the installation checklist and then set the Enhanced Security Mode to [ON] again. For details of settings made by the service engineer, contact your service representative.
—When the machine is to be discarded or use of a leased machine is terminated at the end of the leasing contract, the administrator should use the Overwrite HDD Data function and the Overwrite All Data function to thereby prevent data to be protected from leaking.
Operation and control of the machine
The administrator should perform the following operation control.
—The administrator should log off from the Administrator Mode whenever the operation in the Administrator Mode is completed. The administrator of the machine should also make sure that each individual user logs off from the User Authentication mode after the operation in the User Authentication mode is completed, including operation of the Secure Print document, User Box, and User Box file.
—During user registration and box registration, the administrator should make sure that the correct settings are made for the correct users, including functional restrictions and box attributes.
—The administrator should set the Encryption Key and FW Update (USB) Password according to the environment, in which this machine is used.
—The administrator should appropriately control the device certificate (SSL certificate) registered in the machine.
—The administrator should ensure that no illegal connection or access is attempted when the machine is to be connected to an external interface.
—The administrator should appropriately control the file of Job Log (Audit Log) data downloaded to, for example, a PC and ensure that none other than the administrator of the machine handle it.
—The administrator should check the Job Log (Audit Log) data at appropriate timing, thereby determining whether a security compromise or a faulty condition has occurred during an operating period.
—When generating or deleting Job Log (Audit Log) and Job Log (Audit Log) data, the administrator should check conditions of using this machine by the user.

|
1.3 |
Precautions for Operation Control |
1 |
—The administrator should make sure that each individual user updates the OS of the user’s terminal and applications installed in it to eliminate any vulnerabilities.
—The administrator should set the account track and make sure that the machine is operated through operative association with the account track.
—The administrator should delete cache following the procedure specified for each browser when seeing previews on a web browser because the contents can be cached on PCs and make sure that users perform the same procedure.
—The administrator must not select a modem method when setting CS Remote Care.
—The administrator should make sure that a USB device is not illegally connected to the machine.
The administrator disables the following functions and operates and manages the machine under a condition in which those functions are disabled.
|
Function Name |
Setting Procedure |
|
IP Address Fax Function * |
Using [Administrator Settings] — [Network Settings] — [Network Fax Set- |
|
tings] — [Network Fax Function Settings], set [IP Address Fax Function] to |
|
|
[OFF]. |
|
|
Internet Fax Function * |
Using [Administrator Settings] — [Network Settings] — [Network Fax Set- |
|
tings] — [Network Fax Function Settings], set [Internet Fax Function] to |
|
|
[OFF]. |
|
|
Relay User Box |
Using [Administrator Settings] — [Fax Settings] — [Function Settings] — |
|
[Function ON/OFF Setting], set [Relay RX] to [OFF]. |
|
|
File Re-TX Box |
Using [Administrator Settings] — [Fax Settings] — [Function Settings], set |
|
[Incomplete TX Hold] to [No]. |
|
|
PC-Fax Permission |
Using [Administrator Settings] — [Fax Settings] — [Function Settings], set |
|
[PC-Fax Permission Setting] to [Restrict]. |
|
|
ID & Print Delete after Print |
Using [Administrator Settings] — [System Settings] — [User Box Settings], |
|
Setting |
set [ID & Print Delete after Print Setting] to [Always Delete]. |
|
User Box Settings |
Using [Administrator Settings] — [System Settings] — [User Box Settings], |
|
set [Allow/Restrict User Box] to [Prohibit]. |
|
|
Report Settings |
Using [Administrator Settings] — [Fax Settings], set all report output set- |
|
tings of [Report Settings] to [OFF]. |
|
|
Bulletin Board User Box |
• Do not create [Bulletin Board User Box] using [Utility] — [One- |
|
Touch/User Box Registration] — [Create User Box]. |
|
|
• Do not create [Bulletin Board User Box] using [Administrator Settings] |
|
|
— [One-Touch/User Box Registration] — [Create User Box]. |
|
|
Delete Other User Jobs |
Using [Administrator Settings] — [System Settings] — [Restrict User Ac- |
|
cess] — [Restrict Access to Job Settings], set [Delete Other User Jobs] to |
|
|
[Restrict]. |
|
|
RAW Port Number |
Using [Administrator Settings] — [Network Settings] — [TCP/IP Settings] — |
|
[RAW Port Number], set [Port 1 to Port 6] to [OFF]. |
|
|
FTP TX Settings |
Using [Administrator Settings] — [Network Settings] — [FTP Settings], set |
|
[FTP TX Settings] to [OFF]. |
|
|
SMB Settings |
• Using [Administrator Settings] — [Network Settings] — [SMB Settings], |
|
set [Client Settings] to [OFF]. |
|
|
• Using [Administrator Settings] — [Network Settings] — [SMB Settings], |
|
|
set [SMB Server Settings] to [OFF]. |
|
|
• Using [Administrator Settings] — [Network Settings] — [SMB Settings], |
|
|
set [WINS/NetBIOS Settings] to [OFF]. |
|
|
• Using [Administrator Settings] — [Network Settings] — [SMB Settings], |
|
|
set [Direct Hosting Setting] to [OFF]. |
|
|
E-Mail RX (POP) |
Using [Administrator Settings] — [Network Settings] — [E-Mail Settings], set |
|
[E-Mail RX (POP)] to [OFF]. |
|
|
SNMP Settings |
Using [Administrator Settings] — [Network Settings], set [SNMP Settings] |
|
to [OFF]. |
|
|
TCP Socket Settings |
• Using [Administrator Settings] — [Network Settings] — [Forward] — [TCP |
|
Socket Settings], set [TCP Socket] to [OFF]. |
|
|
• Using [Administrator Settings] — [Network Settings] — [Forward] — [TCP |
|
|
Socket Settings], set [TCP Socket (ASCII Mode)] to [OFF]. |
|

|
1.3 |
Precautions for Operation Control |
1 |
|||
|
Function Name |
Setting Procedure |
||||
|
SSL/TLS Version Setting |
Start the Web Connection and, using [Security] — [PKI Settings] — [SSL |
||||
|
Setting] of the administrator mode, cancel the selection of [SSLv3] of |
|||||
|
[SSL/TLS Version Setting]. |
|||||
|
WebDAV Settings |
• Using [Administrator Settings] — [Network Settings] — [WebDAV Set- |
||||
|
tings], set [WebDAV Client Settings] to [OFF]. |
|||||
|
• Using [Administrator Settings] — [Network Settings] — [WebDAV Set- |
|||||
|
tings], set [WebDAV Server Settings] to [OFF]. |
|||||
|
DPWS Settings (Printer Set- |
• Using [Administrator Settings] — [Network Settings] — [DPWS Settings], |
||||
|
tings/Scanner Settings) |
set [Printer Settings] to [OFF]. |
||||
|
• Using [Administrator Settings] — [Network Settings] — [DPWS Settings], |
|||||
|
set [Scanner Settings] to [OFF]. |
|||||
|
LPD Setting |
Using [Administrator Settings] — [Network Settings] — [Detail Settings], set |
||||
|
[LPD Setting] to [Disable]. |
|||||
|
Remote Access Setting |
Using [Administrator Settings] — [Network Settings], set [Remote Access |
||||
|
Setting] to [OFF]. |
|||||
|
LLMNR Setting |
Using [Administrator Settings] — [Network Settings] — [TCP/IP Settings], |
||||
|
set [LLMNR Setting] to [Disable]. |
|||||
|
AirPrint |
Using [Administrator Settings] — [Authorization function Setting] — [Install |
||||
|
License] — [Function Code], prohibit entering the AirPrint-enabling code |
|||||
|
and enabling AirPrint. |
|||||
|
Bonjour Setting |
Using [Administrator Settings] — [Network Settings], set [Bonjour Setting] |
||||
|
to [OFF]. |
|||||
|
Mopria Setting |
Using [Administrator Settings] — [Network Settings] — [Mopria Setting], set |
||||
|
[Terminal Request Response Setting] to [OFF] and do not to set it to [ON]. |
|||||
|
Send Domain Limit Settings |
Using [Administrator Settings] — [Network Settings], set [Send Domain |
||||
|
Limit Settings] to [Do Not Limit] and do not to set it to [Limit]. |
|||||
|
LLTD Setting |
Using [Administrator Settings] — [Network Settings] — [Detail Settings] — |
||||
|
[Device Setting], set [LLTD Setting] to [Disable] and do not to set it to [En- |
|||||
|
able]. |
|||||
|
Personal Data Security Set- |
Using [Administrator Settings] — [Security Settings] — [Security Details], set |
||||
|
tings |
[Job History] and [Current Job] under [Personal Data Security Settings] to |
||||
|
[Yes]. |
|||||
*: It will not be displayed in case of service mode where the setting is not configured (the function is set to OFF when it is not displayed).
Machine Maintenance Control
The administrator should perform the following maintenance control activities.
—Provide adequate control over the machine to ensure that only the Service Engineer is able to perform physical service operations on the machine.
—Provide adequate control over the machine to ensure that any physical service operations performed on the machine by the Service Engineer are overseen by the administrator.
—Some options require that Enhanced Security Mode be turned [OFF] before they can be used on the machine. If you are not sure whether a particular option to be additionally purchased is fully operational with the Enhanced Security Mode turned [ON], contact your Service Representative.
—Install the machine at a safe site that can be monitored and operate and manage the machine while ensuring that the machine is protected from unauthorized physical access.
Precautions for using the printer driver
The following precautions should be used when the printer driver is to be used in this machine:
—When a document is to be transmitted from the PC to the machine, user registration is necessary in advance.
—With the external server authentication, a user is registered in this machine when he or she has been successful in identification authentication on the control panel.
—Any document that has been transmitted by a user who is yet to be registered is discarded.

1.4Miscellaneous
Password Rules
Study the following table for details of the number and types of characters that can be used for each password. For details of the settings of the Password Rules, see page 2-15.
|
Types of |
Number of |
Types of characters |
Conditions for set- |
|
|
passwords |
characters |
ting/changes |
||
|
Administrator |
8 to 64 |
• |
Numeric characters: 0 to 9 |
• A password only consist- |
|
Password |
characters* |
• |
Alpha characters: upper and |
ing of identical charac- |
|
lower case letters |
ters cannot be registered |
|||
|
User Password |
||||
|
• |
Symbols: !, #, $, %, &, ‘, (, ), |
or changed. |
||
|
Account Password |
*, ,, -, ., /, :, ;, <, =, >, ?, @, [, |
• The current password |
||
|
, ], ^, _, `, {, |, }, ~, + |
must be entered before a |
|||
|
Public User Box |
||||
|
• Special characters (98 char- |
change can be made in |
|||
|
Password |
acters) |
the setting. |
||
|
Annotation User |
Selectable from among a total of |
• A new password to be |
||
|
191 characters |
set should not be the |
|||
|
Box Password |
||||
|
same as the current one. |
||||
|
Secure Print |
8 to 64 |
• |
Numeric characters: 0 to 9 |
• A password only consist- |
|
Password |
characters* |
• |
Alpha characters: upper and |
ing of identical charac- |
|
lower case letters |
ters cannot be |
|||
|
• |
Symbols: !, #, $, %, &, ‘, (, ), |
registered. |
||
|
*, ,, -, ., /, :, ;, <, =, >, ?, @, [, |
||||
|
, ], ^, _, `, {, |, }, ~, +, SPACE |
||||
|
Selectable from among a total of |
||||
|
94 characters |
||||
|
Confidential RX |
8 characters |
• |
Numeric characters: 0 to 9 |
• A password only consist- |
|
password |
• |
Symbols: *, # |
ing of identical charac- |
|
|
ters cannot be registered |
||||
|
or changed. |
||||
|
FW Update (USB) |
0 to 20 |
• |
Numeric characters: 0 to 9 |
• A new password needs |
|
Password |
characters |
• |
Alpha characters: upper and |
to be re-entered. |
|
lower case letters |
||||
|
• |
Symbols: !, #, $, %, &, ‘, (, ), |
|||
|
*, ,, -, ., /, :, ;, <, =, >, ?, @, [, |
||||
|
, ], ^, _, `, {, |, }, ~, +, SPACE |
||||
|
Selectable from among a total of |
||||
|
94 characters |
||||
|
Memory RX User |
1 to 8 |
• |
Numeric characters: 0 to 9 |
• The password rules are |
|
Box Password |
characters |
not applicable. |
||
|
Encrypted PDF |
— |
— |
• The password rules are |
|
|
Password |
not applicable. |
|||
|
• Password that is set |
||||
|
when PDF document is |
||||
|
created. |
||||
*: The minimum number of characters set in [Set Minimum Password Length] must be set for the password. The default value is 12.
Precautions for Use of Umlaut
—Setting or entering an umlaut from the control panel may be disabled depending on the setting made in this machine, but not on the client PC side including Web Connection. If an umlaut is set in a password on the PC side, therefore, the umlaut cannot be entered from the control panel, which means that this particular password is not usable.

Precautions for Use of Various Types of Applications
Comply with the following requirements when using the Web Connection or an application of various other types
The administrator should make sure that the user observes the following requirements.
—The password control function of each application stores the password that has been entered in the PC being used. Disable the password management function of each application and perform an operation without storing a password.
Use a web browser or an application of various other types that shows «*» or «-» for the password entered.
—Once the password has been entered, do not leave your PC idle without logging on.
—Set the web browser so that cache files are not saved.
—Do not access any other site once you have logged onto the machine with the Web Connection. Accessing any other site or a link included in e-mail, in particular, can lead to execution of an unintended type of operation. Whenever access to any other site is necessary, be sure first to log off from the machine through the Web Connection.
—Using the same password a number of times increases the risk of spoofing.
—If a web browser such as Internet Explorer is used on the client PC side, «TLS v1.0» or more should be used for the SSL setting.
—Optional applications not described in this User’s Guide are not covered by certification of ISO15408.
Encrypting communications
This machine guarantees encrypted communication via IPsec.
IPsec setting
This machine offers a choice of two authentication methods of [Pre-Shared Key] and [Digital Signature] for authenticating the remote machine with which to communicate.
When [Pre-Shared Key] is to be used, control the pre-shared key appropriately to ensure that it is not leaked to any third party other than the remote machine with which to communicate. For the shared key, set a value that consists of a combination of eight or more alphanumeric characters and that cannot be easily guessed. Do not set a value that can be easily guessed from your birthday, employee identification number, and the like.
[Digital Signature] has a higher security strength than [Pre-Shared Key].
The ISO15408 evaluation for the machine is performed on the basis of the [Pre-Shared Key].
Do not use DES or 3DES in the encryption algorithm of [IKE Settings]. Use AES. [Main Mode] and [Aggressive Mode] are available in [Negotiation Mode]. The default setting is [Main Mode]. The administrator should operate the machine with the [Main Mode] setting.
Leaking the pre shared key for IPsec set on the MFP increases the risk of spoofing of the MFP, etc. Therefore, set machine-specific pre shared keys and manage them safely.
An illegal DNS response (e.g., a response exceeding 2048 bytes) made by the DNS server may cause the TOE to perform an unexpected operation. The administrator should control such that the DNS server does not make such a response. It should also be noted that setting of multiple DNS servers increases the risk.
Note that unencrypted communication can be established if the IPsec setting is not made over the whole address range (0 to 255 for IPv4) and an IP address outside the range is assigned to a client PC.
Select an ESP Encryption Algorithm from AES-GCM, AES-CBC, and AES-CTR for IPsec SA Settings. Furthermore, when AES-CBC or AES-CTR is selected, select an ESP Authentication Algorithm from SHA-1, SHA-2, and AES-XCBC.
NOTICE
The administrator of the machine should make sure that SSL encryption communication is not performed with the SSL set in SSL v3.
Do not use an SSL certificate that is electronically signed by MD5, as an increased risk results of data to be protected being tampered with or leaked.
To eliminate the risk of the data to be protected being tampered with or leaked, refer to the recommended ciphers list disclosed by, for example, NIST and CRYPTREC and use the appropriate cryptographic technique.

Use the following browsers to ensure safety. Use of any of the following browsers achieves communication that ensures confidentiality of the image data transmitted and received.
Microsoft Internet Explorer
—9/10/11
Mozilla Firefox
—20 or later
Microsoft Internet Explorer 11 is used for the ISO15408 evaluation for this machine.
Print functions
Only the following procedures are guaranteed for the print functions performed from the client PC.
—Use IPPS printing for the print functions performed using the printer driver.
—Use direct printing from the Web Connection for the print functions not performed via the printer driver.
IPP printing
IPP (Internet Printing Protocol) is a function that allows printing via the Internet by using the HTTP (HyperText Transfer Protocol) of the TCP/IP Protocol. IPPS (IPP over SSL/TLS) is the type of IPP that performs the SSL encryption communication.
<Installing printer driver>
To perform IPPS printing, the printer driver must be installed. Start the printer addition wizard of the Windows Vista/7/8/8.1/Server 2008/Server 2008 R2/Server 2012/Server 2012 R2 and type [DNS Host Name] and [Default DNS Domain Name] of this machine in the following format in the «URL» field.
https://[DNS host name].[default DNS domain name]/ipp
For [DNS host name] and [default DNS domain name], specify the names set with the DNS server.
<Registering the certificate in Windows Vista or later>
Windows Vista or later, which offers enhanced security functions, gives a certificate error message if the SSL certificate is one that is not issued by a certification body. In such cases, it becomes necessary to register the certificate of this machine as that issued by a reliable party for the computer account.
First, register Host Name and IP address of this machine in the DNS server in advance. Then, in TCP/IP Settings of Web Connection, set the DNS Host Name and DNS Default Domain Name registered with the DNS server.
It should also be noted that, for the certificate to be imported, a certificate for SSL encryption communication should be registered in Web Connection and exported in advance as the certificate including the public key.
1From «Continue to this website,» call the Web Connection window to the screen.
2Click «Certificate Error» to display the certificate. Then, click «Install Certificate» to install the certificate.
3Display the physical stores. Then, deploy the certificate, which has earlier been exported, in «Local Computer» of «Trusted Root Certification Authorities» to thereby import the certificate.

Items of Data Cleared by Overwrite All Data Function
The Overwrite All Data function clears the following items of data.
|
Items of Data Cleared |
Description |
|
Password Rules |
Sets [Disable] and disables [Set Minimum Password Length] |
|
User registration data |
Deletes all user-related data that has been registered |
|
Account track registration data |
Deletes all account track-related data that has been registered |
|
Box registration data/file |
Deletes all User Box-related information and files saved in User Box |
|
Secure Print ID/Password/ |
Deletes all Secure Print document-related information and files saved |
|
document |
|
|
ID & Print document |
Deletes all ID & Print documents saved in ID & Print User Box |
|
Image files |
• Image files other than Secure Print documents, ID & Print docu- |
|
ments, and User Box files |
|
|
• Data files left in the HDD data space, used as image files and not |
|
|
deleted through the general deletion operation |
|
|
• Temporary data files generated during print image file processing |
|
|
Destination recipient data files |
Deletes all destination recipient data including e-mail addresses and |
|
telephone numbers |
|
|
Encryption Key |
Clears the currently set Encryption Key |
|
Administrator Password |
Clears the currently set password, resetting it to the factory setting |
|
(1234567812345678) |
|
|
FW Update (USB) Password |
Clears the currently set FW Update (USB) Password |
|
Device certificate |
Deletes the currently set Device certificate (SSL certificate) |
|
(SSL certificate) |
|
|
SSL encryption strength |
Deletes the SSL certificate to thereby clear the SSL encryption |
|
strength |
|
|
SSL-compliant protocol |
Makes the protocol not complying with SSL |
|
Network Setting |
Clears the currently set network settings (DNS Server setting, IP Ad- |
|
dress setting, and SMTP Server setting), resetting it to the factory set- |
|
|
ting |
|
|
Daylight Saving Time |
Set to [No] |
|
Time Adjustment Setting (NTP) |
Set to [OFF] |
|
Time/date data |
Varies corrected data, if the time-of-day data is corrected due to, for |
|
example, the daylight saving time |
|
Fax functions
An optional Fax Kit is required for using fax functions. Contact your Service Representative.
USB keyboard
The USB keyboard is not used for the ISO15408 evaluation for this machine.
Do not use a USB keyboard.

Different types of boxes
A box may be a user box or a system box. The user can store documents in the User Box. Also, the user can print a file from the User Box or send a file to another user. The System Box is used by the system to temporarily store files when the user uses the facsimile or print function together with the file storage function of the box.
The User Box (*) cannot be used under the operation and control of this machine.
|
Type |
Description |
|
Public User Box * |
This is the public box in which all users can store documents and use |
|
them. Note that a password is set for the box and the set password |
|
|
needs to be entered before access can be gained to the box. |
|
|
Personal User Box * |
This is a personal box. Only users who have logged in to the system |
|
can store and use documents in the Personal User Box. |
|
|
Group User Box * |
This is a group box. Only users belonging to the same department (or |
|
group) can store and use documents in the Group User Box. |
|
|
Secure Print Box |
When you print a document from the PC or when you select the Se- |
|
cure Print function using the printer driver, this data file is stored in the |
|
|
Secure Print User Box. |
|
|
Memory RX Box |
When a facsimile is received by the Memory RX function, it is stored |
|
in the Memory RX User Box. |
|
|
ID & Print Box |
When you print a document from the PC, the files transferred with the |
|
ID & Print function are stored in the ID & Print User Box. |
|
|
Annotation User Box |
When a stored file is printed out or sent to another user, its date, time |
|
and any annotations are added to this box automatically. |
|
|
Password Encrypted PDF Box |
When a password protected PDF file is printed out or stored in the |
|
User Box, the file is stored in the Password Encrypted PDF User Box. |
|
Hardware and software used in the machine
The following lists the software, hardware, and their versions used for the ISO15408 evaluation for this machine and they are the same as those listed on the security target.
The ISO15408 evaluation assumes that the HDD is mounted in the machine. Any configuration not including the HDD is not guaranteed by the ISO15408 evaluation.
The user should appropriately manage the hardware and software used with the machine on his or her own responsibility.
|
Hardware/software |
Version, etc. |
|
|
FAX Kit |
FK-514 |
|
|
Printer Driver |
PCL: Ver. 6.1.2.0 |
|
|
PS: Ver. 6.1.2.0 |
||
|
XPS: Ver. 6.1.2.0 |
||
|
Data Administrator with De- |
Ver. 1.0.09000 |
|
|
vice Set-Up and Utilities |
||
|
Data Administrator |
Ver. 4.1.38000 |
|
|
External authentication server |
Active directory mounted on Windows Server 2008 R2 Standard Ser- |
|
|
vice Pack 1 |
||
|
DNS server |
Windows Server 2008 R2 Standard Service Pack1 |
|
Firmware integrity verification function
When the main power switch is turned ON with the Enhanced Security Mode set to [ON], the machine checks the encryption key and the hash value to thereby determine that its firmware is fully operational.
If a fault occurs in the firmware, a malfunction screen appears when the machine is started, warning that a fault has occurred. To reset the fault condition, turn [OFF] the Enhanced Security Mode and restart the machine, or update the firmware. For more details, consult your Service Representative.

CS Remote Care function
CS Remote Care is a system that manages the machine through transmission and reception of various types of data for managing the machine between the machine and the CS Remote Care center computer via a telephone/fax line, a network, or E-mail. Functions are disabled to access the LAN from the telephone line and to directly transfer received fax.
When the Enhanced Security Mode is set to [ON], the following functions are no longer usable: instructing to rewrite the firmware, sending and receiving account counter information, rewriting settings of the machine, and the Counter Remote Control function.
Terminating a Session and Logging out
The machine allows the operator to automatically log out from or terminate a session, if it is unable to detect an operation on the control panel or a communication packet on the network. Additionally, if a user changes the user password on the control panel while the same user accessing the machine via Web Connection, the session of Web Connection is terminated.
The following shows the setting range and the default setting of each function. Set the time according to the environment in which the machine is used.
The administrator should explain to the user that the following settings are made. The administrator should also explain to the user immediately as soon as the setting has been changed.
|
Function name/software, etc |
Description |
|
System Auto Reset |
Setting range |
|
• [1] to [9] minutes, Default setting: [1] minute |
|
|
Setting procedure |
|
|
• [Utility] — [Administrator Settings] — [System Settings] — [Reset Set- |
|
|
tings] — [System Auto Reset] |
|
|
Auto Logout |
Setting range |
|
(Web Connection) |
• [Admin. Mode Logout Time]: [1] to [60] minutes |
|
Default setting: [10] minutes |
|
|
• [User Mode Logout Time]: [1] to [60] minutes |
|
|
Default setting: [60] minutes |
|
|
Setting procedure |
|
|
• Start the Web Connection and, in the Administrator Mode, select |
|
|
[Security] — [Auto Logout]. |
|
|
Data Administrator |
Default setting: [60] minutes (No change can be made in the setting) |
|
The time setting represents consideration for the time-consuming |
|
|
task, such as downloading the registered information. Be careful |
|
|
about leaving your seat, because the time setting is rather long. |
|
Authentication error during external server authentication
If a user is unable to log in successfully during user authentication using the external server authentication, possible causes include the status of connection to the external server, the condition of the external server (the server is down), and the status of user registration with the external server such as the number of users to be controlled by the machine reaching its limit and the user password quality on the external server.
The administrator should check these points and make the appropriate settings.

2 Administrator Operations

|
2.1 |
Accessing the Administrator Mode |
2 |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
2Administrator Operations
2.1Accessing the Administrator Mode
In Administrator Mode, the settings for the machine system and network can be registered or changed.
This machine implements authentication of the user of the Administrator Mode function through the Administrator Password or User Password that verifies the identity as the administrator of the person who accesses the function. During the authentication procedure, the Administrator Password entered for the authentication purpose appears as «*» or «-» on the display.
When the Enhanced Security Mode is set to [ON], the number of times in which authentication fails is counted.
NOTICE
Make sure that none of the general users of the machine will know the Administrator Password.
If the Administrator Password is forgotten, it must be set again by the Service Engineer. Contact your Service Representative.
The user who is given the administrative right by the administrator can access the Administrator Mode when logging on as the user administrator.
2.1.1Accessing the Administrator Mode
The machine does not accept access to the Administrator Mode under any of the following conditions. Wait for some while before attempting to gain access to the Administrator Mode again.
—The Administrator Mode has been logged on to through access made from the PC.
—A remote operation is being performed from an application on the PC.
—There is a job being executed by the machine.
—There is a reserved job (timer TX, fax redial waiting, etc.) in the machine.
—Immediately after the main power switch has been turned ON.
—A malfunction code is displayed on the machine.
<From the Control Panel as the Administrator of the Machine>
0If another administrator has already logged on to the Administrator Mode using Web Connection, the machine displays a message saying that other administrator has logged on and rejects access as the administrator. Wait until the message disappears before attempting to access the Administrator Mode once again.
0When accessing the Administrator Mode from the control panel, if [Export to the device] operation is being executed using the Data Administrator, the machine displays a message that tells not to turn off the power because of the remote operation being performed and rejects any operation on the control panel. Wait until the message disappears before attempting to access the Administrator Mode once again.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.

|
2.1 |
Accessing the Administrator Mode |
2 |
Touch [Utility].
Touch [Administrator Settings].
Enter the Administrator Password from the keyboard.
%Touch [C] to clear all characters.
%Touch [Delete] to delete the last character entered.
%Touch [Shift] to show the upper case/symbol screen.
%Touch [Cancel] to go back to the previous screen.
4Touch [OK].
%If a wrong Administrator Password is entered, a message that tells that the Administrator Password does not match appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
5Press the Reset key to log off from the Administrator Mode.

|
2.1 |
Accessing the Administrator Mode |
2 |
<From the Control Panel as the User Administrator>
1Touch [Operation Rights] to select [Administrator].
Enter the user name and the password, then touch [OK].
Touch [Login] or press the Access key to log in to this machine.
Touch Menu — [Utility] — [Administrator Settings].
The Administrator Mode is displayed. Perform a desired operation. Press the Reset key to log off from the Administrator Mode.

|
2.1 |
Accessing the Administrator Mode |
2 |
<From the Web Connection as the Administrator of the machine>
0If you have already logged on to the Admin Mode from the control panel or using Web Connection, the machine displays a message that tells that another administrator has previously logged on and rejects any attempt to log on to the Admin Mode using the Web Connection. Click [OK] and wait for some while before attempting to access the Admin Mode once again.
0If [Export to the device] operation is being executed using the Data Administrator, the machine displays a message that tells you cannot log on to the mode because of the remote operation being performed and rejects any attempts to the Admin Mode via the Web Connection. Click [OK] and wait for some while before attempting to access the Admin Mode once again.
0Do not leave the machine with the Admin Mode setting screen left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Admin Mode.
0If you have logged on to the Admin Mode using the Web Connection and if you close the web browser without clicking [Logout], the control panel remains locked for 160 sec.
0Different initial screens appear after you have logged on to the Admin Mode depending on the Customize setting. The descriptions herein given are concerned with the display screen set in [Meter Counter] of Maintenance.
1Start the Web browser.
2Enter the IP address of the machine in the address bar.
3Press the [Enter] key to start Web Connection.
4Click the Administrator radio button and [Login].
5Select the «Administrator (Admin Mode)» in the Administrator, and enter the Administrator Password in the «Password» box.

|
2.1 |
Accessing the Administrator Mode |
2 |
%If «Administrator (Admin Mode)» is selected, the settings for the machine system and network can be registered or changed.
%When accessing the Admin Mode using the Web Connection, enter the same Administrator Password as that for the machine.
6Click [OK].
%If a wrong Administrator Password is entered, a message that tells that the authentication has failed appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
7Click [Logout].
8Click [OK].
This allows you to log off from the Admin Mode.

|
2.1 |
Accessing the Administrator Mode |
2 |
<From the Web Connection as the User Administrator>
1Start the Web browser.
2Enter the IP address of the machine in the address bar.
3Press the [Enter] key to start Web Connection.
4Click the Administrator radio button and [Login].
5Select «Administrator (Admin Mode)» in the Registered User and enter the user name in the «User Name» box and the user password in the «Password» box.
%If «Administrator (Admin Mode)» is selected, the settings for the machine system and network can be registered or changed.
%When accessing the Admin Mode using the Web Connection, enter the same User Password as that for the machine.
6Click [OK].
%If a user administrator enters a wrong User Password, a message that tells that the authentication has failed appears. Enter the correct User Password.
%If the Enhanced Security Mode is set to [ON], the entry of a wrong User Password is counted as unauthorized access. If a wrong User Password is entered a predetermined number of times (once to three times) or more set by the administrator, a message appears saying that the machine accepts no more User Passwords because of unauthorized access for any subsequent entry of the User Password. The machine is then set into an access lock state. To cancel the access lock state, the administrator must perform the Release Setting. Contact the administrator.
7Click [Logout].
8Click [OK].
This allows you to log off from the User Administrator Mode.
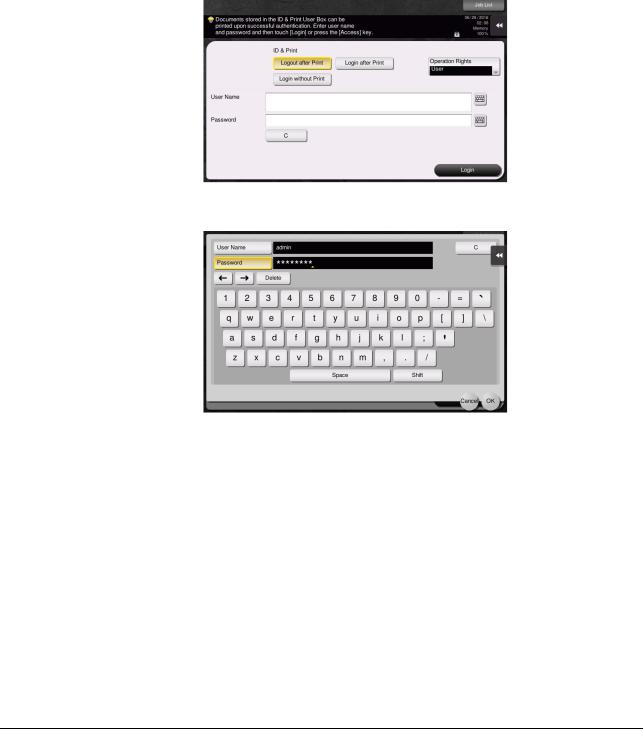
|
2.1 |
Accessing the Administrator Mode |
2 |
2.1.2Accessing the User Mode
You can log on to the User Mode as an administrator. In the User Mode, you can check or delete a job, which is disabled in Administrator Mode.
 Tips
Tips
The authority relating to box settings is the same as that of Administrator Mode.
<From the Control Panel>
0The administrator must first make User Authentication settings before he or she can access User Mode. For details of the User Authentication, see page 2-27.
0Do not leave the machine with the User Mode setting screen left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the User Mode.
1Touch the keyboard icon in the [User Name] field.
2Enter «admin» in [User Name]. Enter the password set for this machine in [Password].
%Touch [C] to clear all characters.
%Touch [Delete] to delete the last character entered.
%Touch [Shift] to show the upper case/symbol screen.
%Touch [Cancel] to go back to the previous screen.
3Touch [OK].

|
2.1 |
Accessing the Administrator Mode |
2 |
4Press the Access key or touch [Login].
%If a wrong Administrator Password is entered, a message that tells that the authentication has failed appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
5Perform a desired operation.
% To delete a job, touch [Job List] and select a target job, and then touch [Delete].
6Press the Access key or touch [Close] to log off from the User Mode.

|
2.1 |
Accessing the Administrator Mode |
2 |
<From Web Connection>
0If you have already logged on to the Admin Mode from the control panel or using Web Connection, the machine displays a message that tells that another administrator has previously logged on and rejects any attempt to log on to the Admin Mode using the Web Connection. Click [OK] and wait for some while before attempting to access the Admin Mode once again.
0If [Export to the device] operation is being executed using the Data Administrator, the machine displays a message that tells you cannot log on to the mode because of the remote operation being performed and rejects any attempts to the Admin Mode via the Web Connection. Click [OK] and wait for some while before attempting to access the Admin Mode once again.
0Do not leave the machine with the Admin Mode setting screen left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Admin Mode.
0If you have logged on to the Admin Mode using the Web Connection and if you close the web browser without clicking [Logout], the control panel remains locked for 70 sec.
0Different initial screens appear after you have logged on to the Admin Mode depending on the Customize setting. The descriptions herein given are concerned with the display screen set in [Meter Counter] of Maintenance.
1Start the Web browser.
2Enter the IP address of the machine in the address bar.
3Press the [Enter] key to start Web Connection.
4Click the Administrator radio button and [Login].
5Select «Administrator (User Mode)» in the Administrator and enter the Administrator Password in the «Password» box.

|
2.1 |
Accessing the Administrator Mode |
2 |
%If «Administrator (User Mode)» is selected, you can log on to the User Mode as an Administrator. In the User Mode, you can check or delete a job, which is disabled in Administrator Mode. Note, however, that the authority relating to box settings is the same as that of Administrator Mode.
%When a user administrator accesses Administrator (User Mode) in the Registered User using Web Connection, enter the User Name and Password.
6Click [OK].
%If a wrong Administrator Password is entered, a message that tells that the authentication has failed appears. Enter the correct Administrator Password.
%If the Enhanced Security Mode is set to [ON], entry of a wrong password is counted as unauthorized access. If a wrong Administrator Password is entered a predetermined number of times (once to three times) or more set by the administrator, a message appears saying that the machine accepts no more Administrator Passwords because of unauthorized access for any subsequent entry of the Administrator Password. The machine is then set into an access lock state.
To cancel the access lock state, settings must be made by the Service Engineer; or, turn off, and then turn on, the main power switch of the machine. If the main power switch is turned off and on, the access lock state is canceled after the lapse of time set for [Release Time Settings]. When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. If there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
Click the [Job] tab.
Perform a desired operation.
Click [Logout].
10 Click [OK].
This allows you to log off from the User Mode.

|
2.2 |
Enhancing the Security Function |
2 |
2.2Enhancing the Security Function
When a log-on to the Administrator Mode becomes successful, the machine enables setting of the Enhanced Security Mode that allows settings for enhancing each of different security functions to be converted all at once.
In the Enhanced Security Mode, the machine allows selection of whether to use the Enhanced Security Mode or not. If the Enhanced Security Mode is set to [ON], a count is taken of the number of unauthorized accesses to the Administrator Authentication, User Authentication, Account Track, all Secure Print, and all User Boxes. A function is also set that determines whether each password meets predetermined requirements. The security function is thus enhanced in the Enhanced Security Mode.
The following settings must first be made before the Enhanced Security Mode is set to [ON].
NOTICE
First, set the Encryption Key. To set the Encryption Key, HDD Format must first be executed. Execution of the HDD Format clears various setting values. For details of items that are cleared by HDD Format, see page 2-14.
If initialization is executed by the Service Engineer, the Password Rules are set to [Disable] and the Administrator Password is reset to the factory setting (1234567812345678). To set the Administrator Password and turn [ON] the Enhanced Security Mode again.
|
Settings to be Made in Advance |
Description |
|
Administrator Password |
Meet the Password Rules. |
|
The factory setting is «1234567812345678.» |
|
|
User Authentication |
Check that [Authenticate] (the server type is Active Directory only |
|
for External Server Authentication) is set. |
|
|
Encryption Key |
Set the Encryption Key. |
|
Certificate for SSL |
Register the self-signed certificate for SSL communications. |
|
Service settings |
Calls for setting made by the Service Engineer. For details, contact |
|
your Service Representative. |
|
Setting the Enhanced Security Mode to [ON] changes the setting values of the following functions.
NOTICE
If an attempt is made to change a setting that has been changed as a result of setting the Enhanced Security Mode to [ON], a screen may appear indicating that the Enhanced Security Mode is to be canceled. Note that executing this screen will cancel the Enhanced Security Mode.
The description «not to be changed» given in parentheses in the table below indicates that the specific setting cannot be changed with the Enhanced Security Mode set to [ON].
|
Function Name |
Factory Setting |
When Enhanced Security Mode is set to [ON] |
|
Password Rules |
Disable |
Enable (not to be changed) |
|
* If [Enable] is set for Password Rules, the types and |
||
|
number of characters to be used for each password are |
||
|
limited. |
||
|
For details of the Password Rules, see page 1-13. |
||
|
Prohibited Functions |
Mode 1 |
Mode 2 (not to be changed): Three times is set. |
|
When Authentication Er- |
* The number of times can be changed to once, twice, |
|
|
ror |
or three times. |
|
|
Release Time settings |
5 min. |
The setting value should be 5 min. or more (no value less |
|
than 5 can be set) |
||
|
Confidential Document |
Mode 1 |
Mode 2 (not to be changed) |
|
Access Method |
* In association with Prohibit Functions When Authenti- |
|
|
cation Error, the method is changed from authentication |
||
|
using Secure Print ID and password (Mode 1) to that us- |
||
|
ing the password with the Secure Print document first |
||
|
narrowed down by Secure Print ID (Mode 2). |
||
|
Secure Print User Box |
Thumbnail View, |
Only Detail View is enabled before password authenti- |
|
Preview |
Detail View, and |
cation (Mode 2) |
|
Document De- |
||
|
tails are enabled |
||
|
Public User Access |
Restrict |
Restrict (not to be changed) |

|
2.2 |
Enhancing the Security Function |
2 |
|||
|
Function Name |
Factory Setting |
When Enhanced Security Mode is set to [ON] |
|||
|
User Name List |
OFF |
OFF (not to be changed) |
|||
|
Print Without Authentica- |
Restrict |
Restrict (not to be changed) |
|||
|
tion |
|||||
|
User Box Administrator |
Restrict |
Restrict (not to be changed) |
|||
|
Setting |
|||||
|
Mode using SSL/TLS |
None |
Admin. Mode and User Mode (not to be changed) |
|||
|
SSL Encryption Strength |
AES-256, |
AES/3DES (not to be changed to one containing |
|||
|
3DES-168, |
strength lower than AES/3DES) |
||||
|
RC4-128 |
|||||
|
FTP Server |
ON |
OFF (not to be changed) |
|||
|
Print Data Capture |
Allow |
Restrict (not to be changed) |
|||
|
Network Setting Clear |
Enabled |
Restrict |
|||
|
(Web Connection) |
|||||
|
Registering and Chang- |
Allow |
Restrict (not to be changed) |
|||
|
ing Address by the user |
|||||
|
(Address Book and Pro- |
|||||
|
gram) |
|||||
|
Initialize (Network Set- |
Enabled |
Restrict (not to be changed) |
|||
|
tings) |
|||||
|
Image Log Transfer Set- |
OFF |
OFF (not to be changed) |
|||
|
tings |
|||||
|
CS Remote Care |
Usable |
Remote device setting disabled |
|||
|
Counter Remote Control |
Restrict |
Restrict (not to be changed) |
|||
|
Remote Panel Settings |
OFF |
OFF (not to be changed) |
|||
|
(Server Settings/Client |
|||||
|
Settings) |
|||||
|
Print Simple Auth. |
Restrict |
Restrict (not to be changed) |
|||
|
(Authentication Setting) |
|||||
|
External Application |
Yes |
No (not to be changed) |
|||
|
Connection |
|||||
|
E-mail RX Print |
OFF |
OFF (not to be changed) |
|||
|
Machine Update Settings |
No |
No (not to be changed) |
|||
|
IWS Settings |
OFF |
OFF (not to be changed) |
|||
|
HDD backup data Set- |
Restrict |
Restrict (not to be changed) |
|||
|
tings |
|||||
|
USB Connection Permis- |
Allow |
Restrict |
|||
|
sion setting |
|||||
|
QR Code Display Setting |
OFF |
OFF (not to be changed) |
|||
|
Enable NFC |
OFF |
OFF (not to be changed) |
|||
|
URL Home Settings |
Enable |
Disable |
|||

|
2.2 |
Enhancing the Security Function |
2 |
2.2.1Items cleared by HDD Format
Following are the items that are cleared by HDD Format.
Whenever HDD Format is executed, be sure to set the Enhanced Security Mode to [ON] again.
|
Items of Data Cleared |
Description |
|
Enhanced Security Mode |
Set to [OFF] |
|
Device certificate |
Deletes the device certificate (SSL certificate) registered in the machine |
|
(SSL certificate) |
|
|
SSL encryption strength |
Deletes the SSL certificate to thereby clear the SSL encryption strength |
|
SSL-compliant protocol |
Makes the protocol not complying with SSL |
|
User Authentication |
Set to [OFF] |
|
Account Track Authentica- |
Set to [OFF] |
|
tion |
|
|
User Box Administrator |
Set to [Restrict] |
|
User Name List |
Set to [OFF] |
|
Print Simple Auth. |
Set to [Restrict] |
|
Print Without Authentica- |
Set to [Restrict] |
|
tion |
|
|
User registration data |
Deletes all user-related data that has been registered |
|
Account Track registration |
Deletes all account track-related data that has been registered |
|
data |
|
|
Box registration data/file |
Deletes all User Box-related information and files saved in User Box |
|
Secure Print ID/Pass- |
Deletes all Secure Print document-related information and files saved |
|
word/document |
|
|
Destination recipient data |
Deletes all destination recipient data including e-mail addresses and tele- |
|
files |
phone numbers |
|
Audit log |
Deletes the audit log |

|
2.2 |
Enhancing the Security Function |
2 |
2.2.2Setting the Password Rules
0 For the procedure to call the Administrator Mode on the display, see page 2-2.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
NOTICE
Before enabling the Password Rules, change the currently set password so as to meet the Password Rules. For details of the Password Rules, see page 1-13.
Call the Administrator Mode on the display from the control panel.
Touch [Forward].
Touch [Security Settings].
4Touch [Security Details].
5Touch [Password Rules].

|
2.2 |
Enhancing the Security Function |
2 |
6Select [Enable] and set [Set Minimum Password Length] (8 to 64 characters).
%The following screen appears if the previously required settings are yet to be made by the Service Engineer. Contact your Service Representative.
7Touch [OK].

|
2.2 |
Enhancing the Security Function |
2 |
2.2.3Setting the Enhanced Security Mode
0For the procedure to call the Security Settings screen on the display, see steps 1 through 3 of page 2-15.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
0The Enhanced Security Mode is factory-set to [OFF]. Be sure to turn [ON] the Enhanced Security Mode so as to enable the security function of the machine.
1Call the Security Settings screen on the display from the control panel.
2Touch [Enhanced Security Mode].
3Select [ON] to enable the Enhanced Security Mode and touch [OK].
%The following screen appears if the previously required settings are yet to be made by the administrator. Make the necessary settings according to the corresponding set procedure.

|
2.2 |
Enhancing the Security Function |
2 |
%The following screen appears if the previously required settings are yet to be made by the Service Engineer. Contact your Service Representative.
4Any external applications registered using OpenAPI will be deleted when the Enhanced Security Mode is set to [ON]. A confirmation message appears. Select [Yes] and touch [OK].
5Make sure that a message appears prompting you to turn OFF and then ON the main power switch. Now, turn OFF and then turn ON the main power switch.
%When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. if there is no wait period between turning the main power switch off, then on again, the machine may not function properly.

|
2.2 |
Enhancing the Security Function |
2 |
%If the Enhanced Security Mode is properly set to [ON], a key icon appears at the portion on the screen enclosed by a red frame, indicating that the machine is in the Enhanced Security Mode.

|
2.3 |
Protecting Machine from Illegal Firmware Update |
2 |
2.3Protecting Machine from Illegal Firmware Update
When a log-on to the Administrator Mode becomes successful, this machine enables the operation of setting or changing the password required to update the firmware, which is performed by a service engineer using a USB memory.
By setting the FW Update (USB) Password, the firmware of the machine can be protected from illegal update. The FW Update (USB) Password entered is displayed as «*.»
NOTICE
The following shows setting conditions for the FW Update (USB) Password. Perform settings for the FW Update (USB) Password fitting these conditions.
|
Types of passwords |
Number of |
Types of characters |
Conditions for set- |
|
|
characters |
ting/changes |
|||
|
FW Update (USB) Pass- |
0 to 20 char- |
• |
Numeric characters: 0 to |
A new password needs |
|
word |
acters |
9 |
to be re-entered. |
|
|
• |
Alpha characters: upper |
|||
|
and lower case letters |
||||
|
• |
Symbols: !, #, $, %, &, ‘, |
|||
|
(, ), *, ,, -, ., /, :, ;, <, =, >, |
||||
|
?, @, [, , ], ^, _, `, {, |, }, ~, |
||||
|
+ |
||||
|
Selectable from among a to- |
||||
|
tal of 93 characters |
||||
Setting the FW Update (USB) Password
<From the Control Panel>
0For the procedure to call the Security Settings screen on the display, see steps 1 through 3 of page 2-15.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
Call the Security Settings screen on the display from the control panel.
Touch [FW Update (USB) Perm. Sett.].

|
2.3 |
Protecting Machine from Illegal Firmware Update |
2 |
3Touch [Password Priority].
4Enter the new FW Update (USB) Password from the keyboard.
To prevent entry of a wrong password, enter the password again in [Password Confirmation].
%Touch [C] to clear all characters.
%Touch [Delete] to delete the last character entered.
%Touch [Shift] to show the upper case/symbol screen.
%Touch [Cancel] to go back to the Security Settings screen.
5Touch [OK].
%If the entered FW Update (USB) Password does not meet the Password Rules, a message that tells that the entered FW Update (USB) Password cannot be used appears. Enter the correct FW Update (USB) Password. For details of the Password Rules, see page 1-13.

|
2.3 |
Protecting Machine from Illegal Firmware Update |
2 |
<From Web Connection>
0 For the procedure to access the Admin Mode, see page 2-2.
0Do not leave the machine with the Admin Mode setting screen left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Admin Mode.
Start Web Connection and access the Admin Mode.
Click the [Security] tab.
3In the menu, set [USB Update] to [Password Priority] in [FW Update (USB) Permission Setting].
4Select the «Password is changed» check box.
Enter the new FW Update (USB) Password. Then, to make sure that you have entered the correct new password, enter the new FW Update (USB) Password once again.
5Click [OK].
%If the entered FW Update (USB) Password in the [Password] box does not meet the Password Rules, a message that tells that the entered FW Update (USB) Password cannot be used appears. Enter the correct FW Update (USB) Password. For details of the Password Rules, see page 1-13.

|
2.4 |
Preventing Unauthorized Access |
2 |
2.4Preventing Unauthorized Access
When a log-on to the Administrator Mode becomes successful, the machine enables setting of the operation of Prohibited Functions When Authentication Error. The machine takes a count of the cumulative number of unsuccessful accesses from each interface to the Administrator Authentication, User Authentication, Account Track, Secure Print authentication, and User Box authentication to prohibit the authentication operation.
Either [Mode 1] or [Mode 2] can be selected for Prohibited Functions When Authentication Error. The factory setting is [Mode 1]. If the Enhanced Security Mode is set to [ON], the setting is changed to [Mode 2] (check count: three times). It is nonetheless possible to change the check count to select from among once, twice, or three times.
If [Mode 2] is selected, the Release Time Settings function is enabled. When the Administrator Authentication is set into the access lock state, the main power switch is turned off and on and, after the lapse of a predetermined period of time after the machine is turned on again, the access lock state of the Administrator Authentication is canceled. The Release Time Settings function allows the period of time, after the lapse of which the access lock state of the Administrator Authentication is canceled, to be set in the range between 1 and 60 min. The factory setting is 5 min. For details of each mode, see the table below.
|
Mode |
Description |
|
Mode 1 |
If authentication fails, the authentication operation (entry of the password) is prohibited |
|
for 5 sec. |
|
|
Mode 2 |
If authentication fails, the authentication operation (entry of the password) is prohibited |
|
for 5 sec. The number of times, in which authentication fails, is also counted and, when |
|
|
the failure count reaches a predetermined value, the authentication operation is prohib- |
|
|
ited and the machine is set into an access lock state. |
|
NOTICE
For details of boxes subject to the User Box authentication, see page 1-17.
If the access lock state of the Administrator Authentication is canceled by the Service Engineer, the setting of the Release Time Settings function is not applied.
Making any of the following settings when the Enhanced Security Mode is set to [ON] will cancel the Enhanced Security Mode.
—Changing [Prohibited Functions When Authentication Error] to [Mode 1]
—Changing the check count for [Prohibited Functions When Authentication Error] to four times or more
—Setting [Release Time Settings] to 1 to 4 min.
Setting Prohibited Functions When Authentication Error
0For the procedure to call the Security Settings screen on the display, see steps 1 through 3 of page 2-15.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
Call the Security Settings screen on the display from the control panel.
Touch [Security Details].

|
2.4 |
Preventing Unauthorized Access |
2 |
Touch [Prohibited Functions When Authentication Error].
Touch [Mode 2].
%Select [Mode 2] when the Enhanced Security Mode is set to [ON]. Selecting [Mode 1] will cancel the Enhanced Security Mode.
%Set three times or less when the Enhanced Security Mode is set to [ON]. Setting four times or more will cancel the Enhanced Security Mode.
%To change the check count, touch [+] to increase the count or [-] to decrease it.
5Touch [Release Time Settings].
6Touch [C] and, from the keypad, enter the time, after the lapse of which the access lock state of the Administrator Authentication is canceled.
%Touch [Display Keypad] to display the keypad.
%Release Time can be set to any value between 1 min. and 60 min. in 1-min. increments. An input data error message appears when any value falling outside the range of 1 to 60 min. is set. Enter the correct Release Time.
%Set 5 min. or more when the Enhanced Security Mode is set to [ON]. Setting 1 to 4 min. will cancel the Enhanced Security Mode.
7Touch [OK].

|
2.5 |
Canceling the Operation Prohibited State |
2 |
2.5Canceling the Operation Prohibited State
When a log-on to the Administrator Mode becomes successful, the machine enables the operation of Release Setting performed for canceling the state of Prohibited Functions When Authentication Error (access lock state) as a result of unauthorized access.
Release Setting clears the unauthorized access check count for all User Authentication, Account Track, all Secure Print authentication, and all User Box authentication, resetting it to zero and canceling the operation prohibited state. Perform the following procedure to cancel the operation prohibited state.
|
Operation Prohibited State |
Canceling procedure |
|
|
Administrator Authentication |
The operation prohibited state is canceled after the main power |
|
|
switch is turned off and on and the period of time set in [Release |
||
|
Time Settings] elapses. |
||
|
User/Account authentication |
The Administrator touches [Release] to cancel the operation pro- |
|
|
hibited state. |
||
|
Secure Print authentication |
||
|
User Box authentication |
||
NOTICE
For details of boxes subject to the User Box authentication, see page 1-17.
Never allow any general user to know the Administrator Password.
Forgetting the Administrator Password requires that a setting be made by the service engineer. Call your Service Representative.
It is also possible for the service engineer to cancel the state of Prohibited Functions When Authentication Error (access lock state) of the Administrator Authentication. Contact your Service Representative.
Performing Release Setting
0For the procedure to call the Prohibited Functions When Authentication Error screen on the display, see steps 1 through 3 of page 2-23.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
0When the main power switch is turned off, then on again, wait at least 10 seconds to turn it on after turning it off. if there is no wait period between turning the main power switch off, then on again, the machine may not function properly.
1Call the Prohibited Functions When Authentication Error screen on the display from the control panel.
2Touch [Release].

|
2.5 |
Canceling the Operation Prohibited State |
2 |
3Select the function, for which Prohibit Function as a result of unauthorized access is to be released.
% The Remote Panel function cannot be used when the Enhanced Security Mode is set to [ON].
4Touch [OK].
This clears the unauthorized access check count of the specific function selected in step 4 and cancels the operation prohibited state.

|
2.6 |
Setting the Authentication Method |
2 |
2.6Setting the Authentication Method
When a log-on to the Administrator Mode becomes successful, the machine enables setting of the authentication method for User Authentication and for Account Track.
The following three types of authentication methods available for User Authentication.
|
Mode |
Description |
|
[ON (MFP)] |
The authentication function of this machine is used for user authenti- |
|
cation. |
|
|
[External Server Authentication] |
Interacts with the authentication server used for user authentication in |
|
(Active Directory only) |
the operating environment. |
|
[Main + External Server] (Active |
The authentication function of the machine may also be used, in con- |
|
Directory only) |
sideration of a possible problem occurring in the external authentica- |
|
tion server. |
|
 Related setting (for the administrator)
Related setting (for the administrator)
The Account Track authentication method may be set to [ON] or [OFF]. If [ON] is selected, be sure to set «Synchronize» in «Synchronize User Authentication & Account Track».
NOTICE
Changing the Account Track setting erases all user and account information data that has previously been registered. At this time, Personal User Boxes owned by the users who are deleted and Group User Boxes owned by the accounts that are deleted may be deleted or changed to Public User Boxes.
If the boxes are changed to Public User Boxes and if the password set for a particular box before this change does not meet the Password Rules, no access can be made to the Public User Box, to which that specific box was changed. In this case, the administrator must first newly set a password that meets the Password Rules. For details of the Password Rules, see page 1-13.
If [External Server Authentication] is selected for the authentication method, be sure to select [Active Directory] in the External Server Settings.
2.6.1Setting the Authentication Method
0 For the procedure to call the Administrator Mode on the display, see page 2-2.
0Do not leave the machine with the setting screen of Administrator Mode left shown on the display. If it is absolutely necessary to leave the machine, be sure first to log off from the Administrator Mode.
Call the Administrator Mode on the display from the control panel.
Touch [User Authentication/Account Track].
 Loading…
Loading…
